You can't secure what you can't see.
Even if it's invisible to you, it's visible to them. Attackers spend weeks in reconnaissance, cataloging your forgotten subdomains, abandoned S3 buckets, and orphaned cloud instances that your teams have lost track of. While you're patching the servers you know about, they're pivoting through the staging environment that's been running unmonitored for six months.
The visibility gap in IT arises from cloud adoption and complex digital assets, allowing attackers to exploit unmanaged infrastructure. An autonomous SOC leverages AI to continuously monitor all assets, automating threat detection and enabling security teams to focus on strategic defense. However, an autonomous SOC hinges on complete, accurate data, moving beyond alerts or generic logs.
True visibility comes through rich, native telemetry from endpoints, networks, clouds, and identities, understood field by field. Cortex reveals end-to-end attack paths by unifying data from code to cloud to SOC, merging enterprise and cloud security. Yet, collection is only half the battle. This raw telemetry must be integrated, stitched, and normalized to form a cohesive, contextualized narrative.
Comprehensive data is what makes everything else possible, from high-fidelity detection and intelligent alert grouping to AI-driven risk scoring and deeper investigative context. By illuminating every detail, you can detect, assess, and stop threats in record time.
In this blog, we’ll explore why traditional SIEMs struggle to deliver full visibility, and how Cortex XSIAM offers a better approach to the areas where legacy SIEMs fell short. Because when your data is complete, so are your defenses.
Connecting the Dots Across Your Digital Estate
Imagine trying to piece together a complex story using only headlines from different sources, in different languages. That's what traditional SIEMs often deliver. They can collect data, but don’t know what it means or how it all fits together.
That’s why controlling and understanding the data matters. As a security platform provider, Palo Alto Networks owns the most critical data sources for detection and response, including endpoint, network, cloud, SaaS and AI security, browser access, vulnerability management, and more. We can always collect the right telemetry needed to stop threats, without gaps or guesswork.
Take the Cortex XDR agent: it delivers up to 3x more telemetry than most EDR or XDR agents. While others filter out data when they don’t detect an attack, Cortex gives you the full picture for threat hunting and forensics. And our Next-Gen Firewalls go further than traditional firewalls, capturing not just network traffic, but user, application, and device-level detail. Enhanced application logs, which include DNS, DHCP, and URL data, are expressly designed to improve detection accuracy of Cortex XSIAM.
Beyond our own robust telemetry, Cortex XSIAM is an open platform designed to ingest and unify data from virtually any source across your security ecosystem. This means you can bring in telemetry from your existing tools and infrastructure, ensuring truly comprehensive visibility and maximizing your security investments.
Because we collect and understand rich telemetry, we can stitch it together with greater precision. Data stitching combines related endpoint, network, cloud, and identity events together to create unified, enriched records. Unlike basic SIEM correlation, stitching evaluates multiple elements of each event for higher accuracy, enabling better cross-data analytics, improved detection, and faster investigations.
Data stitching also powers SmartGrouping, which automatically consolidates related alerts into meaningful cases. Using SmartGrouping, deduplication, and exclusions, the Palo Alto Networks SOC cuts 25,000 alerts down to just 75 actionable cases every day, on average. SmartGrouping can help overwhelmed SOC teams reclaim dozens, or even hundreds, of hours each week by streamlining triage and analysis.
Faster Investigations with Greater Context
Data stitching also speeds up investigations by connecting events together to reveal the full scope and impact of an attack. Cortex XSIAM does not just focus on isolated alerts, it builds a clear picture of an attack.
For example, a firewall alert might show a suspicious connection, while endpoint data reveals the process that triggered it, and identity logs show login attempts from the same device at the same time.The firewall tells you what happened. The endpoint shows how. Identity data explains who was involved.
Together, they form a complete, cohesive narrative of an incident. Without blind spots, or fragments, such as individual SIEM alerts. Cortex products provide the context your analysts need to investigate and stop threats before damage is done.
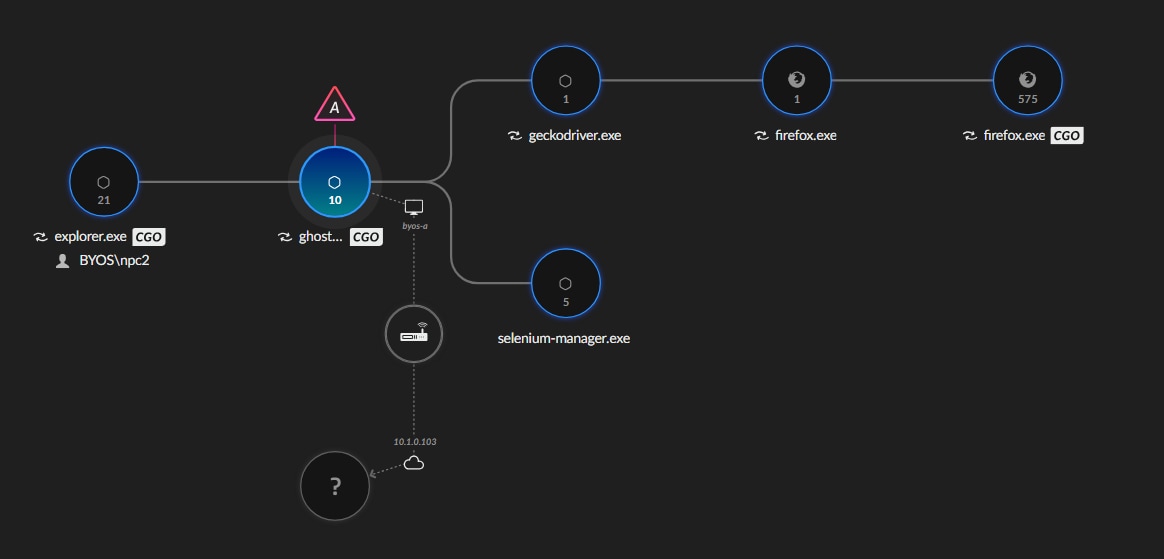
Data stitching is not just about grouping alerts. It builds a rich, interconnected view that enhances visibility and improves every stage of detection, investigation and response.
From Alerts to Action
With such a rich data foundation, the next challenge is to make sense of the myriad of enriched events. This is where SmartGrouping comes in. SmartGrouping leverages the power of this stitched data to extract even more artifacts and, critically, improve the correlation of individual alerts into meaningful, actionable cases.
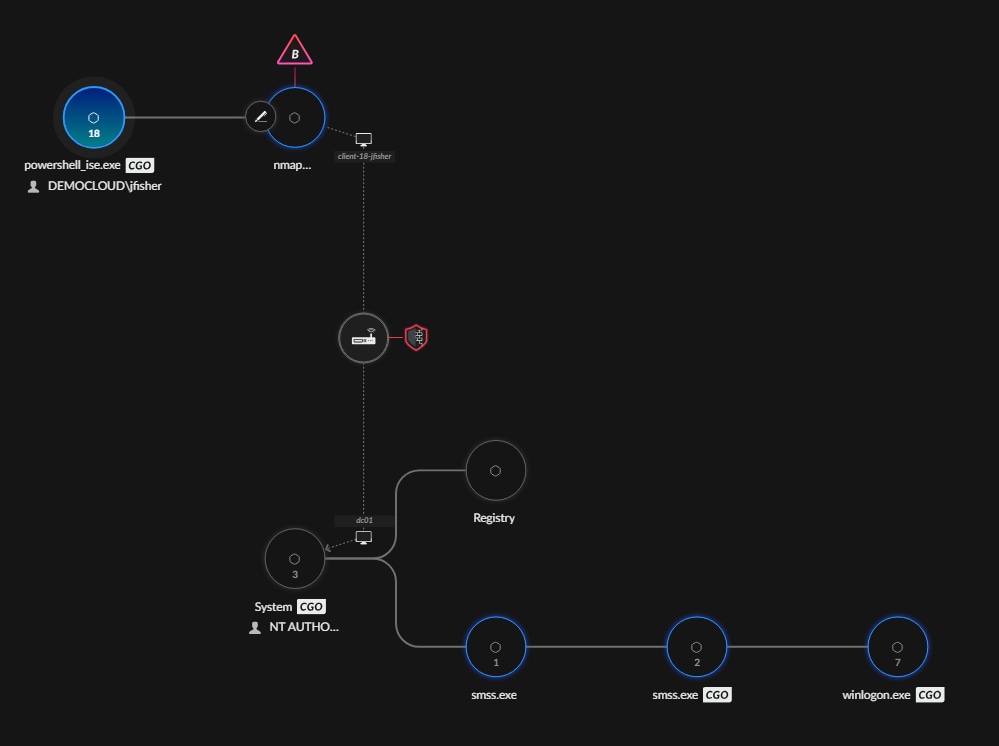
Consider our previous example: a firewall alert stitched with detailed process information from the endpoint. With SmartGrouping, that process context becomes a powerful pivot point. The system can now surface additional related artifacts, such as files, registry changes, or user activity. More importantly, it links other alerts with similar process characteristics into the same incident.
Instead of forcing analysts to sift through hundreds of isolated alerts, SmartGrouping consolidates them into a small number of high-fidelity cases. This dramatically reduces alert fatigue, speeds up investigations, and gives analysts the full context needed to understand the scope and impact of an attack.
This rich, integrated, and contextualized data foundation is also crucial for robust automation. It empowers security orchestration, automation, and response (SOAR) playbooks to execute with precision, allowing routine tasks and initial responses to be handled automatically, freeing up your security team for more complex threats.
The Data Advantage
Cortex XSIAM delivers a powerful advantage by starting with rich, complete data that's deeply understood, whether it originates from our own robust telemetry sources or is ingested from any other security tool or infrastructure across your environment. Delivering:
- Complete Visibility: No blind spots. High-fidelity telemetry from endpoint, network, and cloud is stitched into a unified view.
- High-Fidelity Detection: Many of our thousands of prebuilt rules and analytics are tightly aligned to our own data, letting SOC teams surface real threats without tuning or noise.
- Faster Investigations: Analysts spend less time chasing clues and more time acting on clear, connected insight.
- Reduced Alert Fatigue: Alerts are enriched and grouped into meaningful cases, shrinking the alert backlog and highlighting what matters.
- Enhanced Context: Deep insights into the "who, what, when, where, and how" of an attack enable more informed decision-making.
By gathering rich telemetry, pinpointing stealthy threats, and grouping related issues into high-fidelity cases, Cortex XSIAM empowers security teams to shift from reactive alert-chasing to proactive, incident-driven defense, improving efficiency and resilience against even the most sophisticated attacks.
See how Cortex can transform your security operations today. Request a personalized demo.