The Invisible Crisis in Your Security Operations
Picture this: your security team is drowning in an ocean of alerts while sophisticated attackers move through your environment undetected. Each security tool—endpoint protection, email gateways, network monitors, cloud security platforms—generates its own stream of data in incompatible formats. Your analysts spend their days playing detective, manually connecting dots across disconnected systems while threats evolve at machine speed.
This isn't just an operational headache—it's a critical security gap that attackers actively exploit. According to Unit 42's Global Incident Response Report 2025, 75% of security incidents had evidence scattered across logs, but data silos prevented detection. Even more alarming, research from the same report shows that in nearly one in five cases, data exfiltration now occurs within the first hour of compromise, giving security teams minimal time to detect and respond.
When identity becomes the beachhead for sophisticated attacks, only a unified, AI-ready data foundation can deliver the timely, cross-domain detection that modern threats demand. The siloed security architectures of the past simply cannot keep pace with today's identity-driven attacks.
Real-World Impact: The Atlas Lion Campaign
The sophisticated tactics of Atlas Lion (also tracked as STORM-0539) perfectly demonstrate why unified data matters. This financially motivated threat actor has perfected cloud-first, long-dwell identity operations, particularly targeting retail organizations through a methodical four-stage approach.
- Initial Access: Atlas Lion launches carefully crafted phishing and smishing campaigns directing victims to counterfeit Microsoft 365 portals—tailored, convincing replicas designed to harvest credentials from specific targets.
- Reconnaissance: Once inside, attackers methodically mine SharePoint and OneDrive repositories for organizational charts, workflow documentation, and remote access guides, building a detailed operational map of the target organization.
- Lateral Movement: Armed with this intelligence, Atlas Lion launches internal phishing campaigns from compromised Office 365 mailboxes. These communications appear to come from trusted colleagues, making them exceptionally difficult to identify as threats.
- Persistence: The attackers establish multiple stealth mechanisms: configuring inbox rules to hide activities, moving sent emails to deleted folders, registering rogue authenticator apps, and enrolling unauthorized devices to evade multi-factor authentication.
The Gift Card Angle
Atlas Lion's focus on gift card fraud represents the perfect criminal opportunity: rapid monetization with minimal traceability, weak access controls despite high monetary values, broad internal permissions for business operations, and limited audit logging compared to traditional financial systems.
Detection in Cortex
The Atlas Lion campaign triggered multiple Cortex detection layers:
- Inbox forwarding rule configured from suspicious location
- Sent emails systematically moved to deleted items
- Suspicious SSO access from unusual ASN
- Impossible traveler patterns across authentication events
- Massive SaaS application data downloads
- SSO authentication from new operating system
Why Traditional Architectures Miss These Attacks
The Atlas Lion campaign perfectly illustrates why siloed security architectures fail against sophisticated threats:
Incompatible Data Formats: Email security systems record suspicious login attempts differently than identity providers, making automatic correlation nearly impossible. An endpoint agent might log device enrollment while the email gateway separately flags forwarding rules—but without unified data, these related events appear as isolated incidents.
Timing Drift Across Systems: Events that occur within milliseconds of each other can appear minutes apart across different security tools due to clock synchronization issues and processing delays. This timing drift makes it difficult to reconstruct the true attack sequence and understand causation.
Lost Context in Data Pipelines: Critical contextual information gets stripped away as data moves between tools. A suspicious login might lose its connection to the user's recent email activity or the device's security posture, making it impossible to assess the full risk.
Scale Limitations of Rule-Driven Correlation: Traditional SIEM platforms struggle to correlate data across multiple domains simultaneously. They're forced to choose between comprehensive visibility and fast response times, often sacrificing one for the other.
How Cortex XDL Changes the Game
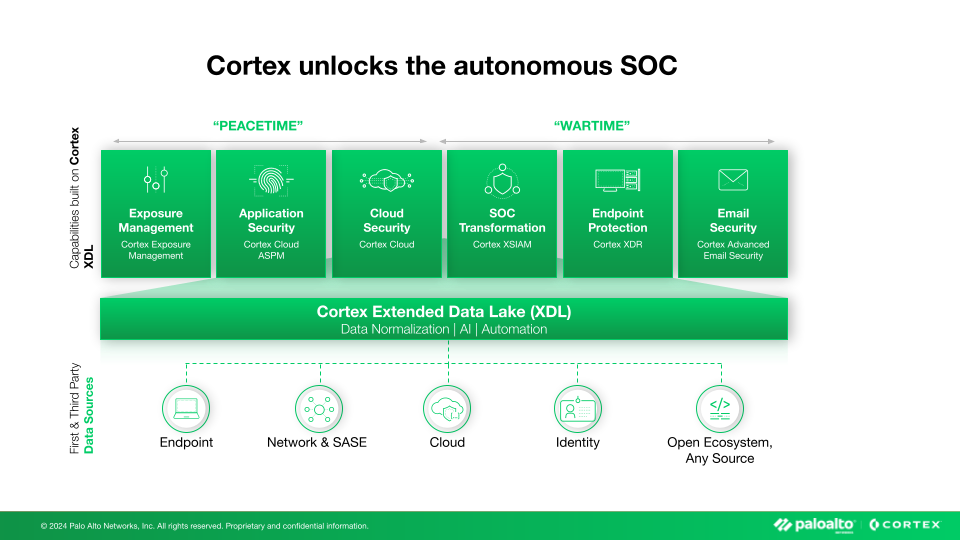
Cortex Extended Data Lake (XDL) fundamentally transforms security operations by creating the industry's most advanced AI-ready security data foundation. This isn't just another data collection system—it's the enabler of truly platformized security operations.
Collect Once, Analyze Infinitely
Cortex XDL's unified approach delivers what we call "collect once, analyze infinitely" efficiency. Rather than each security tool maintaining its own siloed data collection and storage infrastructure, Cortex XDL serves as the foundational data layer—centralizing ingestion while making this rich dataset available to every security module that needs it.
The transformative power lies in having all your security data unified within Cortex XDL's foundation. This comprehensive data lake becomes the bedrock for specialized security modules. When you enable Advanced Email Security, it immediately leverages endpoint and network context already present in the platform. When you deploy Exposure Management, it instantly correlates vulnerability data with actual network activity and user behavior patterns captured across your environment.
As an extensible platform, Cortex XDL doesn't perform detection itself—instead, it empowers a growing ecosystem of purpose-built security modules to tackle any security use case. Each new capability becomes exponentially more powerful because it builds upon the complete, contextualized data foundation that Cortex XDL provides. This architecture ensures that adding new security capabilities enhances rather than fragments your security posture.
Universal Normalization and Stitching
Cortex XDL automatically translates data from hundreds of security tools into a common schema, enabling seamless correlation across previously incompatible systems. Identity events, SaaS activity, email communications, endpoint telemetry, and network traffic all speak the same language, making cross-domain analysis possible for the first time.
Real-Time Enrichment at Ingestion
As data enters Cortex XDL, it's automatically enriched with threat intelligence, asset context, user behavior baselines, and environmental information. This enrichment happens at ingestion time, ensuring that security analysts and AI algorithms always have complete context for every security event.
AI-Optimized Data Structure
Unlike generic data lakes, Cortex XDL structures security data specifically for machine learning algorithms. Pre-computed features, relationship mapping, and behavioral baselines enable AI models to identify subtle attack patterns that would be computationally impossible with raw, unstructured data. This foundation powers over 10,000 pre-built detectors and 2,600 ML models that continuously analyze security events.
Enterprise Scale Without Compromise
Cortex XDL handles 11+ petabytes of security data daily, automatically normalizing and pre-stitching raw telemetry into AI-ready intelligence. The platform maintains sub-second query response times across months of historical data, enabling real-time analysis at unprecedented scale.
The Outcomes You Can Expect
Organizations implementing Cortex XDL see transformational improvements across their security operations:
- 98% reduction in Mean Time to Resolution (MTTR) through automation and unified context that eliminates manual correlation work
- 99% reduction in vulnerability noise as Cortex exposure management leverages unified data to prioritize risks that actually threaten your business
- Discovery of approximately 30% more security tools than teams knew they had, providing comprehensive visibility across previously unknown shadow IT
- Access to 10,000+ pre-built and automatically enabled detectors compared to the 100-200 correlation rules most SOCs maintain internally
The economic impact is equally significant: organizations reduce data storage costs by eliminating redundant tools and data lakes while dramatically improving detection accuracy through full data integration that was previously impossible.
Transform Your Security Operations
Imagine your security analysts arriving at work energized rather than overwhelmed. Instead of facing thousands of disconnected alerts, they see a clear, prioritized view of genuine threats that require their expertise. They spend their time hunting sophisticated adversaries like Atlas Lion and building stronger defenses, not wrestling with data correlation across multiple tools.
This transformation isn't just about technology—it's about giving your people the foundation they need to do their best work. Your team deserves a platform that amplifies their expertise rather than burdening them with busywork.
Ready to see how unified security data transforms threat detection? Experience how Cortex XDL enables comprehensive attack story reconstruction on your own data. Request a demo to see how platformized security operations can defend against today's most sophisticated identity-driven attacks.
Download the Solution Brief today!