Security operations centers (SOCs) today face a formidable challenge: overwhelming alert volumes, sophisticated evasive malware, and the unrelenting pressure for rapid, accurate detection. Traditional signature-based detection and machine learning (ML) models have allowed us to detect more threats than ever before. However, their reliance primarily on simple "malicious" or "benign" labels limits their depth of understanding and adaptability.
Simplistic labeling is a relic from a time when threats were less complex. Today's evasive malware is designed to look benign, using packers, encryption, and multi-stage payloads that only reveal their true nature upon execution. Compounding the problem, legitimate proprietary software often uses the exact same obfuscation and packing techniques to protect intellectual property, appearing suspicious to traditional models. This dual-sided ambiguity places an impossible burden on SOC teams, who are left to guess the severity and function behind each sterile "malicious" flag, slowing response times to a crawl. The fundamental question is no longer if a file is malicious, but how it is malicious.
By combining the best of traditional ML and generative AI, malware detection models can see deeper into executables than a single label. Through automated explanations, detection models are more precise and can evolve faster than ever before.
Making Sense of Arbitrary Contextless Executables Is Hard
While today's advanced machine learning models are powerful tools for identifying malicious behavior, the pursuit of ever-higher accuracy and the detection of novel, evasive threats presents an ongoing challenge. To continue to improve detection rates today, we focus on rare and uniquely crafted samples, as well as on investigating potential mistakes made by the model. It is essential to pinpoint why the elusive corner cases are missed or misclassified, which means understanding why each executable behaves the way it does. The insights we need go beyond a simple label to include: What are an executable’s core capabilities, and what objectives is it attempting to achieve?
Advanced AI Synthesizes Meaningful Explanations of Executables
In order to improve security outcomes for our customers, Palo Alto Networks developed a proprietary AI system that revolutionizes how we analyze and understand executable files and powers a number of our products and services. The synergy between generative AI and classical ML underpins the Precision AI approach. Through combining AI and ML, our malware detection models benefit directly from automatic executable explanations as well as other sophisticated AI techniques. We are building and leveraging the novel advanced solutions that modern cybersecurity demands.
The explanation system ingests an executable and automatically generates a human-understandable description of its key behaviors and capabilities. Think of it as having an army of AI-powered reverse engineers working 24/7, meticulously dissecting files and summarizing their findings.
Automatically generatable explanations go far beyond a simple "malicious" or "benign" classification. Instead, they provide rich, contextual information such as:
- Does the file attempt to establish persistence?
- Does it try to contact known command-and-control servers?
- Is it encrypting files?
- Does it employ specific anti-analysis or obfuscation techniques?
- Is it an instance of a known benign product?
- Is it an installer?
Synthesizing a multitude of facts into a detailed summary of a file’s likely purpose provides invaluable insights for our security researchers and ML development teams to help reduce their work load and help them respond faster to incidents.
Unlike generative AI systems that deal only in text, our multimodal AI for executable explanations delves into the literal bits and bytes of the executable. We start by scrutinizing the executable's static structure: its complete disassembled and decompiled machine code (even parts that might never run in a sandboxed environment) as well as its embedded artifacts and metadata. We then analyze its dynamic footprint by observing what happens when we try to run it and what additional code it leverages.
This holistic approach, combining static and dynamic data, provides clear explanations of the executable's behavior as well as its potential purpose and identity. Through advanced generative AI, we distill higher-level meaning from layers of analysis that build directly on the actual bytes of the executable.
Automatic Explanations Provide More Precise Models, Faster Updates, and Better Protection
Automatic executable explanations herald a new and useful capability for operational teams across Palo Alto Networks and for our customers. One of many positive outcomes is that we can now build and refine our ML malware detection models with a much shorter and more self-assured iteration loop. As a result, Cortex customers are already benefiting from the power of Precision AI, which leverages the strengths of both traditional ML and generative AI.
We Discover and Confirm New Threats Through Automated Explanations
Automated explanations empower us to discover and validate new malware that might evade other detection systems.
For instance, our agent-based maliciousness detection model recently identified a two-year-old sample file as malware. The automatic explanation summary supported the assessment of maliciousness:
The executable downloads and executes shellcode from a remote server. The downloaded shellcode may be encrypted. The executable is a 64-bit Go program compiled for Windows. It has an invalid PE checksum (0) and exhibits signs of packing or code obfuscation. It interacts with various system DLLs related to networking, system functions, power management, user interface, and multimedia. It also queries and interacts with registry keys related to system settings. Decompilation of the executable was unsuccessful, suggesting potential anti-analysis techniques. The executable lacks a cryptographic signature and was first seen on VirusTotal on 2023-05-18.
However, even though our detection model and the explanation text strongly suggested maliciousness, the industry consensus on VirusTotal was that this file was benign. Until our investigation, only about 6% of vendors had given this file a “malicious” verdict.
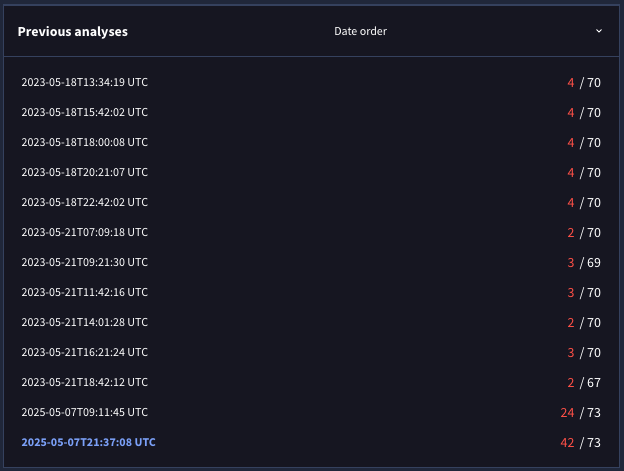
Our ML team needed to resolve the dissonance between (1) our state-of-the-art model asserting that the file was malicious, and (2) the “truth” of industry consensus labels asserting that the file was benign. With the help of an automated explanation that clearly named and explained the behavior of the file, our ML team was independently able to validate that industry consensus was wrong and that the PANW detection model had discovered a new threat.
Because this executable was not flagged in VirusTotal as malicious initially, we suspect this particular sample may have been installed in networks under the radar for nearly 24 months. During this time, even SOC analysts whose tooling provided correct verdicts may have been dismissing alerts on this file as false positives. Once we introduced automated explanations, however, we were able to quickly and independently verify executable behavior and determine its maliciousness.
Stay Ahead of Attackers
True understanding of executables is crucial for staying ahead of attackers. Our detection engines have an edge in identifying evasive attacks because of Precision AI. Precision AI balances depth of understanding with speed. It both deconstructs and explains complex behaviors through generative AI, and it deploys those insights in computationally efficient ways through classical ML.
Precision AI: Cybersecurity Innovation
Precision AI by Palo Alto Networks synergistically incorporates the best of traditional machine learning and modern generative AI in interesting and effective ways. The advanced AI & ML techniques used, like automatic executable explanations, directly translate to more precise and faster malware detection capabilities that products powered by Precision AI utilize. Through our commitment to innovation, your security operations center benefits from smarter, more resilient defenses. We continue to push the boundaries of AI in cybersecurity, enabling our solutions to evolve to meet the challenges of tomorrow, today.
Stay Informed. Stay Safe.
Explore Precision AI : Defend against adversarial AI in real time, secure your organization's GenAI usage and AI-powered application development, and cut down on complexity with AI-driven security copilots.
Learn about our AI-powered threat intelligence: Stay informed about the latest threats and vulnerabilities with our AI-driven threat intelligence service.
Engage with our demos: See our AI cybersecurity solutions in action and learn how they can protect your organization.