A Critical Component of Zero Trust is Ensuring All Application and API Transactions are Legitimate, Safe, and Secure
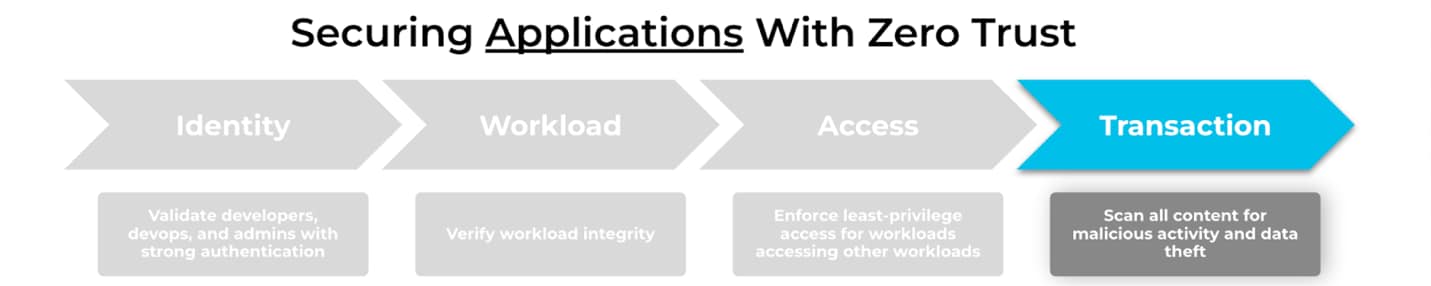
Over the past few years organizations have been adopting cloud computing technologies. With that comes shifting legacy applications on monolithic architectures to building cloud native applications on microservices. By 2023, over 500 million apps will be developed using cloud-native approaches (IDC FutureScape). Organizations moving to the cloud are finding themselves navigating new challenges such as implementing a Zero Trust strategy. Over these years, the concept of zero trust - never trust, always verify - has largely stayed the same. But now cloud architects, devops and security teams face a bigger challenge in securing the content and data when securing the transactions between applications.
Let's take a look at why it is critical to secure all content within transactions on your cloud native applications and how Palo Alto Networks solves this problem.
The State of Applications and Security
The move to the cloud creates more interconnectivity between applications. Modern apps are leveraging microservices and APIs for building scalable and resilient applications, but security teams should not assume all allowed traffic to and from apps contain safe and legitimate content.
According to Forrester, web application exploits, such as SQL injection, cross-site scripting (XSS), and remote file inclusion, are the most common forms of external attacks. And according to AV-Test, over 160 million new malware variants were detected in 2021.
By applying Zero Trust principles to all communications and inspecting the contents of each transaction, organizations can identify and prevent unsafe content from reaching applications.
Applying Zero Trust to Transactions
Embedding Zero Trust in the cloud requires continuous validation at every stage of an application or API interaction. Once access to an application has been verified and granted, the content within the transaction must be inspected to determine it is free of any malicious activity, then only the transaction should be authorized.
The Zero-Trust approach is crucial when verifying the transaction, rather than implicitly trusting the content in the transaction. Adversaries use allowed communications to execute the most common web application attacks like SQL injection and cross-site scripting (XSS) as well as recent attacks including Apache log4j exploit and Cobalt Strike command-and-control (C2) framework. Organizations adopting a Zero Trust architecture should consider verifying every transaction to increase their defenses against malicious activity within content.
How Palo Alto Networks Can Help
At Palo Alto Networks we offer a portfolio designed to deliver on the promise of Zero Trust for applications in the cloud. More specifically, the VM-Series and CN-Series software next generation firewalls (NGFWs) together with Prisma Cloud Web Application and API Security (WAAS) are purposely engineered to secure transactions.
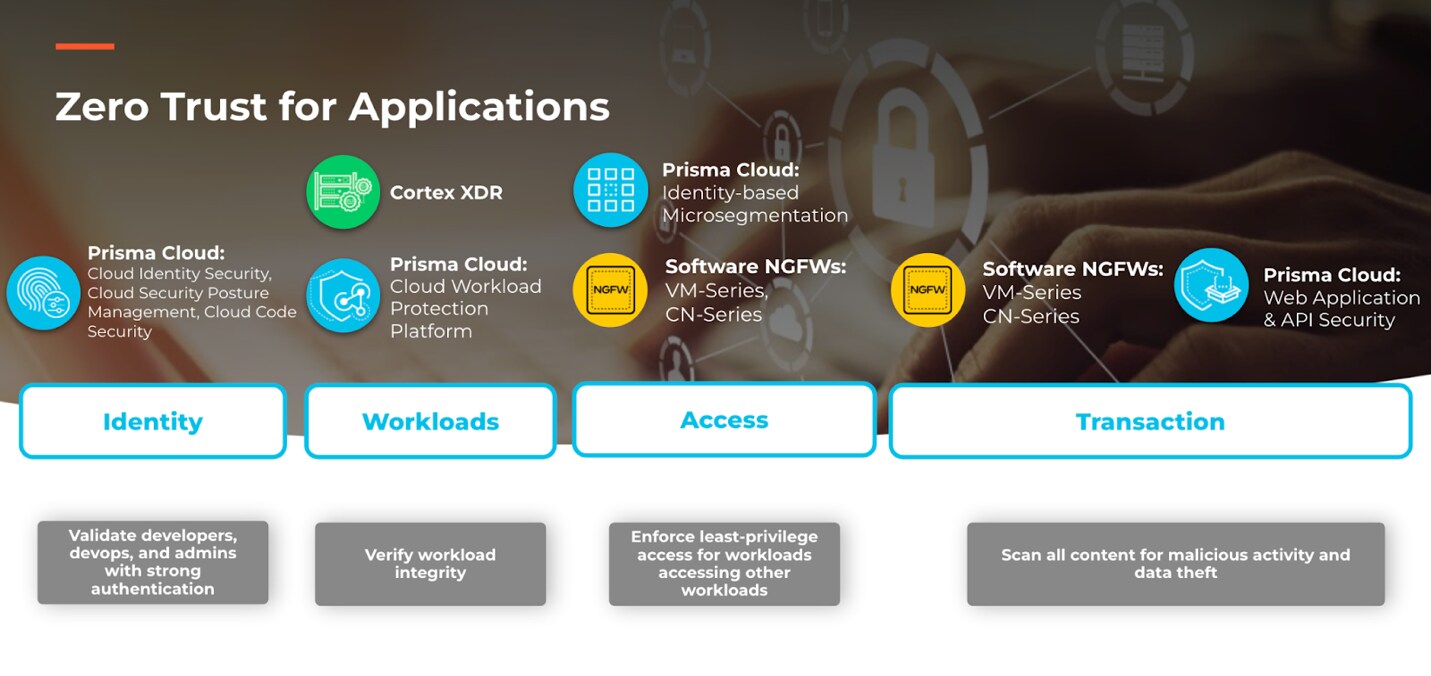
Software NGFWs
The software NGFWs inspect application traffic on your network to ensure every transaction is safe from malicious activity and data theft. This is made possible through the integration with Palo Alto Networks’ industry-leading cloud delivered security services (CDSS).
With Advanced Threat Prevention, the software NGFWs automatically block known malware, vulnerability exploits, and C2 with 100% effectiveness as well as 48% more unknown C2 than the industry’s leading intrusion prevention (IPS) solution.
The Advanced URL Filtering functionality inspects transactions to the internet to block known and unknown malicious URLs.
The Wildfire sandboxing service uses real-time analysis and threat intelligence to automatically identify unknown threats from attacking your application.
The software NGFWs inspect transactions to apply DNS Security. DNS Security automatically detects and blocks sophisticated DNS-based attacks including malicious domains, Domain Generation Algorithm (DGA) attacks, and other DNS threats.
Applying Data Loss Prevention (DLP) ensures the software NGFWs block sensitive data theft attempts.
The software NGFWs are designed with Zero Trust in mind to continuously ensure application transactions in the cloud are free of malicious activity and data theft.
Prisma Cloud
To secure transactions, security teams must understand the cloud native applications they want to protect. Web App and API Security (WAAS) from Prisma Cloud delivers automatic discovery of all web applications and APIs across any cloud native architecture.
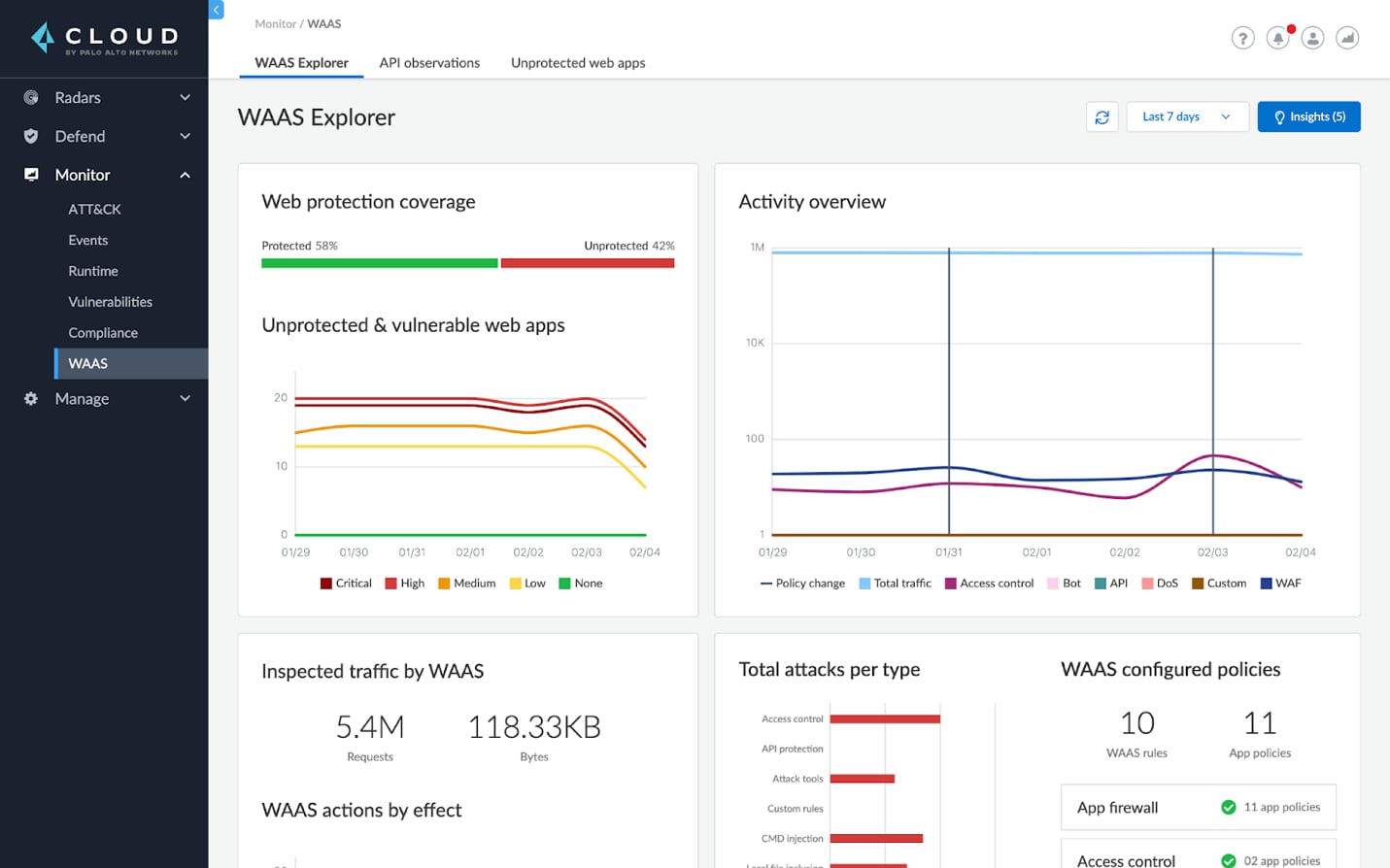
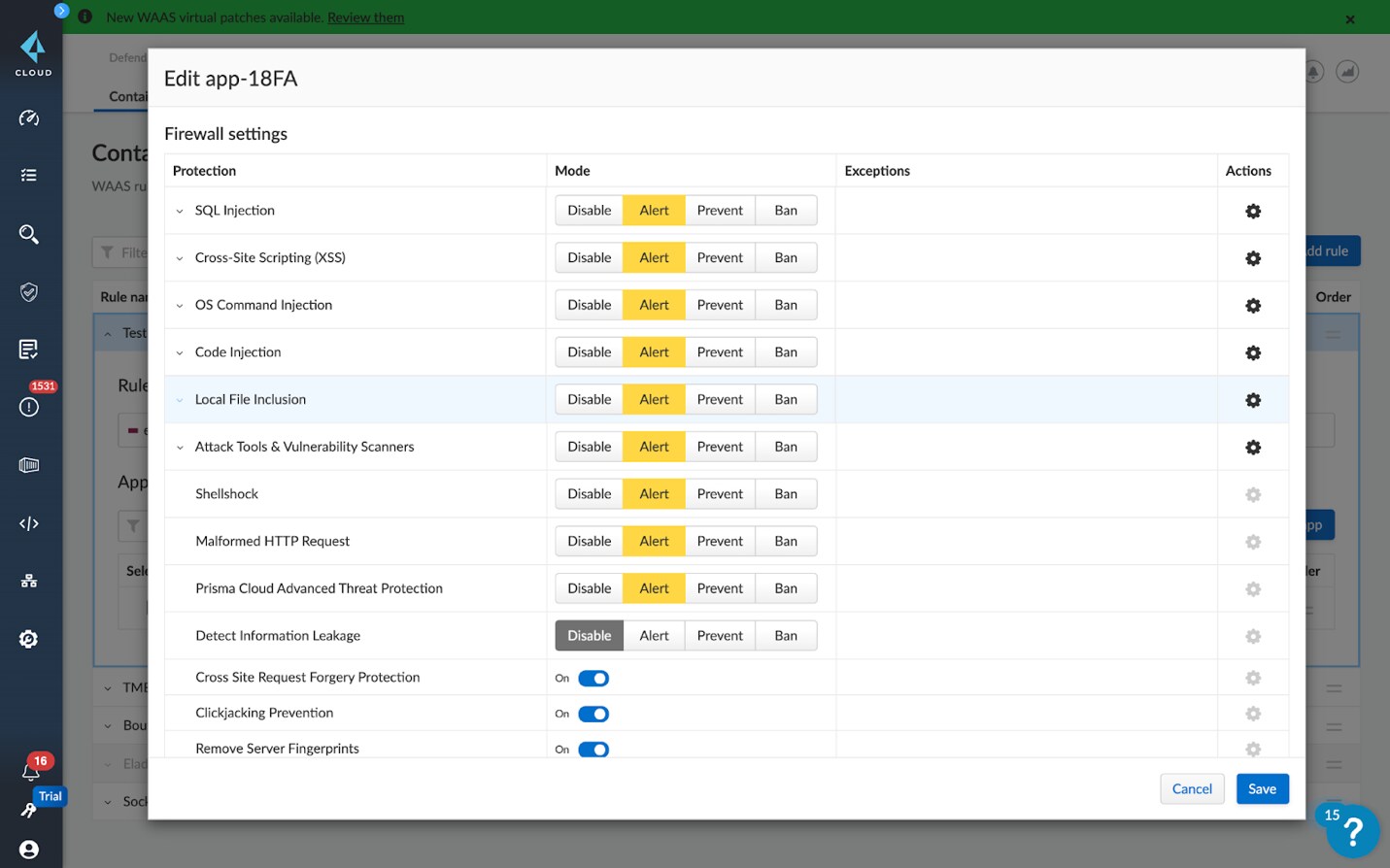
WAAS provides Layer 7 security for all HTTP/HTTPs traffic. The built-in Web App Firewall functionality protects against the top 10 most critical web application security vulnerabilities (OWASP Top 10). Customers can choose from different functionality to alert, prevent or ban against attacks on the application.
Web-facing applications constantly interact with bots on the internet. While not every bot is malicious, organizations can apply Zero Trust principles to secure web-facing transactions. Prisma Cloud verifies every transaction to allow good bots, such as search engine crawlers and news bots, to transact with your applications, but monitor and block abusive bot behavior.
Inspecting transactions is required to protect against Denial of Service (DoS) attacks; to prevent attackers from flooding your applications with large amounts of fake traffic. WAAS is able to enforce rate limits on IPs or sessions to protect against high-rate and "low and slow" application layer DoS attacks.
In a nutshell Prisma Cloud WAAS provides full coverage across OWASP Top 10, advanced DoS threats, bad bots, file upload, access control attacks, and more. A Zero Security model requires that you secure not only the application, but the transactions between that application.
Where can I get started?
Together, Web App and API Security and software NGFWs deliver a Zero Trust solution that secures any application transaction across public cloud, private cloud or hybrid cloud environments.
If you want to get your hands on the software NGFWs, then sign up for an ultimate test drive. If you want to see how Prisma Cloud Web Application and API Security works in your environment, then request a 30-day trial for Cloud Workload Protection.