Serverless architectures have created a new level of abstraction in cloud computing, allowing applications to be built from small, single-purpose pieces of code called functions. Developers frequently leverage third-party code libraries within these functions. Taking the concept one step further, AWS developed Lambda layers that allow separate functions to share a single library, thus reducing the overall size of a function’s package and enabling faster deployment.
While Lambda layers are an incredibly helpful tool for developers, they can also contain vulnerabilities and cause compliance issues. To help customers continue to use these technologies securely, Prisma Cloud now lets users scan Lamba layers as part of their overall serverless function scanning.
What is a Lambda Layer?
In a distributed and event-driven environment, serverless functions usually have a single, dedicated purpose. For example, a function might be used for processing an email or analyzing log messages.
To avoid code duplication, developers will build these functions using third-party code libraries. These libraries are often broadly applicable, meaning that they might be used by multiple functions within an application. So, the next question many developers had was whether they could easily share those libraries easily among functions. That’s exactly what AWS was solving for when it introduced Lambda layers back in 2018.
A Lambda layer is essentially a way to share code and data among functions. It’s a .zip archive that might contain libraries, data, a custom runtime and other dependencies.
Lambda layers have a separate deployment process from the functions themselves. When you deploy your function, you can state in the function’s configuration which specific Lambda layer you want to leverage as part of the function’s execution. In runtime, the Layers are extracted to the /opt directory within the function. You can refer to this path in your function’s code.
Scanning Lambda Layers in Prisma Cloud
When you add a serverless account, the “Scan Lambda Layers” toggle is on by default. All you have to do is onboard your accounts, and Prisma Cloud will do the rest.
The scan results for the Lambda layers will appear in a separate tab, as seen in the screenshot below. Here you can quickly see any specific vulnerabilities or compliance issues that were identified within each layer.
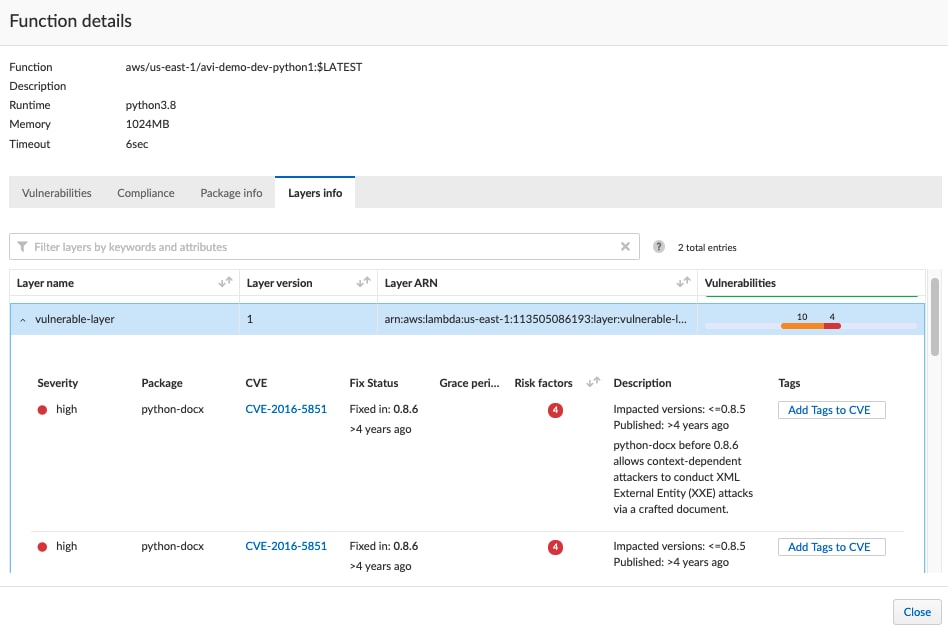
After detecting a vulnerable Lambda layer, the next step would be to search for the functions that utilize that layer. Then you can remediate the issue(s) by deploying a new, updated version of that layer and reconfiguring the functions to point to the updated version.
Conclusion
Using Lambda layers, sharing data and code among functions has never been easier. That said, it’s also easier than ever to share vulnerable libraries among those functions and applications. Serverless scanning with Prisma Cloud helps ensure you don’t neglect your Lambda layers when securing your serverless perimeter.
For technical reference, you can read the serverless function scanning section in our documentation. And you can learn more about securing diverse architectures into runtime with our latest ebook, Why and How to Add Runtime Defense to Your Cloud Security Strategy.