Palo Alto Networks Outperforms Against Cobalt Strike Attacks
Palo Alto Networks is the leading vendor in preventing Cobalt Strike C2 communication. According to the recently published report by SecureIQlab, Palo Alto Networks is the only leader with a block rate of ~99% of tested attacks and the highest Threat Response Efficiency. Please find the report here.
The ever-evolving threat landscape makes it challenging for organizations to be confident in their security posture. Our Unit 42 team has reported more than a 73% increase in attackers using white hat hacking tools to perform command and control attacks, with “Cobalt Strike” as the leading attack. Cobalt Strike can create highly evasive C2 channels, bypassing traditional security methods of blocking with IPS signatures, URL filtering, etc. SecureIQ Lab published a study comparing leading security offerings for Next-Generation Firewalls and SASE products, concluding that Palo Alto Networks is the leading vendor in preventing Cobalt Strike C2 communication with the AI/ML-based Cloud-delivered Advanced Threat Prevention service. The report is based on individual studies for NGFW and SASE products.
Cobalt Strike Explained
Cobalt Strike is a legitimate penetration testing tool intended to be used by white hat hackers to perform penetration tests. With an intuitive UI, even novice threat actors can launch sophisticated command and control attacks such as command line execution, file transfers, keylogging, etc.
Malleable C2 profiles allow the operator to encrypt, encode and otherwise obfuscate network traffic in many different ways to mimic benign flows and even other malware communications. These profiles range from well-known default or basic settings to nearly limitless hand-crafted custom profiles. Traditional signatures can be evaded even for known Cobalt Strike profiles.
Researchers have also created and shared tools to quickly generate new randomized Cobalt Strike profiles. These profiles are highly configurable, small in memory, emit low and asynchronous traffic, and can be masqueraded as different pieces of software, making them difficult to detect.
Due to its flexibility and ease of use, Cobalt Strike is unfortunately being used for malicious purposes by bad actors. A few cracked versions have recently become readily available, skyrocketing their application for illegitimate use.
The traditional approach vendors use static IPS signatures, blocking malicious URLs and domains hosting the C2 server. Based on the SecureIQLab studies, these techniques fail to address new and evasive variants. A new approach is needed to block C2 traffic with Cobalt Strike while avoiding false positives.
See The Only Leader in Exfiltration of Sensitive information Over the Command-and-Control Channel
Traditional IPS signatures cannot distinguish between genuine benign traffic and the one emulated by Cobalt Strike and let the traffic through. Palo Alto Networks’ Advanced Threat Prevention uses ML/AI to detect C2 traffic masqueraded as benign application traffic. Advanced Threat Prevention Service is able to detect and block over 99% of C2 traffic, whereas other leading security services were able to block less than 20% with the traditional approaches.
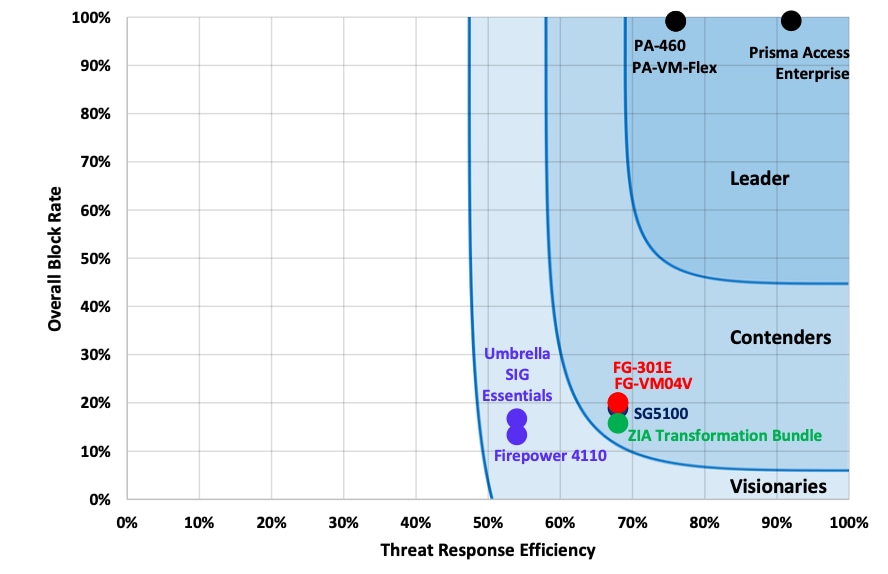
The graphic below from SecureIQLab shows that Palo Alto Networks is the only leader that successfully blocks over 99% of attempted C2 channels using Cobalt Strike.
With cloud-delivered security, a customer can view the logs of an attempted command and control attack, which can be automatically blocked through configurable settings. At the same time, our competitors may allow this traffic.
SecureIQ Lab tested the ability of various security solutions to block the command-and-control capabilities of the Cobalt Strike attack suite. The test measured the block rate of each vendor in five attack scenarios: Basic attack, random attack, custom attack, nonstandard ports-based attack, HTTPS attack and hostname change attack.
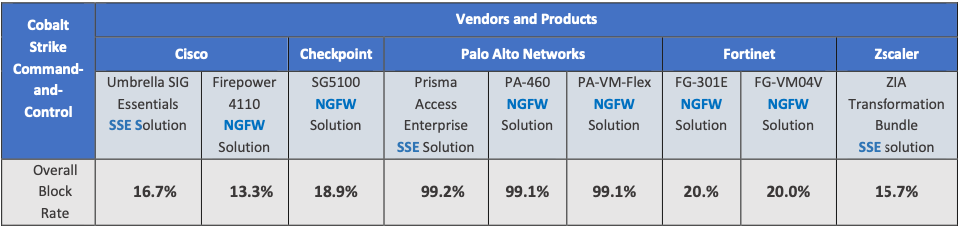
Palo Alto Networks leads all security vendors in preventing Cobalt Strike C2 communication.
Cobalt Strike remains the premier post-exploitation adversary emulator that continues to evade conventional next-generation solutions, including signature-based detection. By design, Cobalt Strike is exceptionally malleable and resilient against static detections. An advanced attacker will have no problem creating completely novel Malleable C2 profiles explicitly designed to thwart static defenses of IPS signatures.
Palo Alto Networks’ Advanced Threat Prevention’s inline deep-learning models and heuristic techniques can prevent Cobalt Strike Beacon and Team Server C2 sessions before exfiltrating a single byte.
Download the full report to learn more.
Related Blogs
Subscribe to Network Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.