Security must keep pace with AI application innovation. Model Context Protocol (MCP) Security is our latest answer — a new capability in Cortex Cloud’s WAAS component that protects the way AI applications interact with sensitive systems through the Model Context Protocol.
What Is MCP and Why Does It Matter?
With remarkable momentum behind its adoption, the Model Context Protocol is quickly becoming the de facto interface for connecting large language models (LLMs) to tools, APIs, databases, and other services. Think of it as the USB-C of AI development — an elegant, standardized bridge that enables dynamic interaction between AI models and external environments. Major AI platforms like ChatGPT, Gemini, and Claude already rely on it. (MCP is in fact Anthropic's creation, a solution designed for Claude Desktop).
Like anything, though, as MCP adoption accelerates, so does the risk. Because MCP connects models to powerful systems and sensitive data in real time, it creates new attack surfaces that conventional security tools weren’t designed to handle.
To meet this challenge, we’ve built MCP Security to safeguard AI communications at their source.
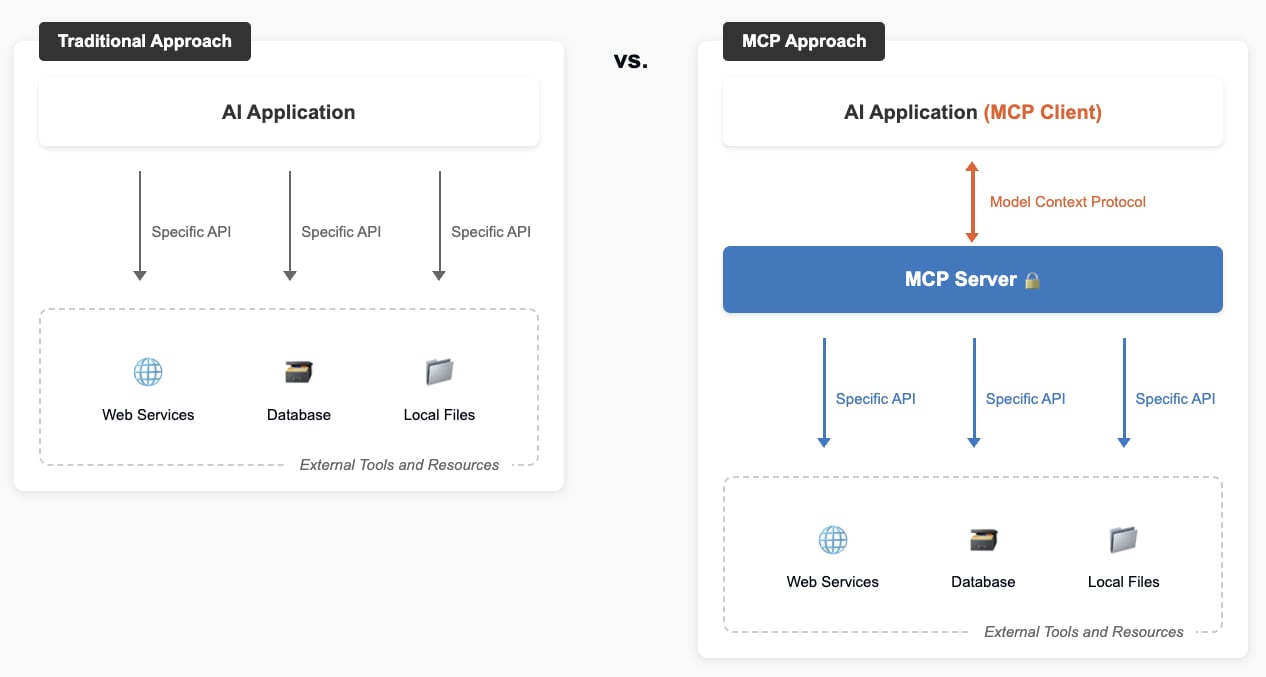
How MCP Works and What It Enables
The Model Context Protocol follows a client-server architecture that defines how AI applications communicate with tools, services, and data sources in real time. It’s not just a bridge — it’s an operational framework that allows LLMs to interact with external environments in structured, context-rich ways.
MCP deployments typically include the following components:
- MCP Hosts: Applications such as Claude Desktop, IDEs, or AI assistants that initiate data access through MCP
- MCP Clients: Components that manage and maintain persistent connections to servers
- MCP Servers: Lightweight services that expose capabilities through the standardized protocol
- Local Data Sources: Files, databases, and services that MCP servers can access within the local environment
- Remote Services: External APIs and internet-connected systems reachable through the protocol
Unlike traditional APIs, MCP supports complex context structures. Applications can pass rich, structured information with each request, expose live data and content to LLMs as Resources, reuse prompt templates called Prompts, enable models to take defined actions through Tools, and request completions through a mechanism called Sampling.
MCP's flexibility and extensibility have made it essential to modern AI development. It underpins enterprise assistants, developer tools, and emerging AI-native interfaces that demand both precision and adaptability.
The Emerging MCP Attack Surface
Because MCP connects large language models to sensitive systems in real time, it makes it an attractive target for attackers. As adoption spreads, several risk categories have emerged.
Protocol Design Vulnerabilities
MCP can expose session identifiers in URLs, rely on inconsistent authentication schemes, and lack standard input validation. These weaknesses open the door to injection attacks.
Centralized Credential Risk
MCP servers often store access tokens for multiple systems. A single compromise can grant attackers lateral access to a wide range of services.
Tool Poisoning Attacks
Attackers can embed hidden prompts or instructions in tool metadata. Although invisible to users, LLMs may interpret these as commands, triggering data exfiltration or unauthorized actions.
Multiserver Conflicts
In environments with multiple MCP servers, organizations risk prompt hijacking, tool name collisions, and uncoordinated server behavior that introduces unpredictable vulnerabilities.
Implementation Level Flaws
Poorly implemented MCP servers often contain command injection flaws, improperly evaluate user input, or lack isolation between processes. These issues can enable privilege escalation and lateral movement.
The bottom line? MCP changes how models interact with the broader environment, but it also introduces a dynamic, high-risk surface. These security challenges are particularly concerning because MCP facilitates communication between powerful AI models and sensitive systems, potentially enabling sophisticated attack vectors that traditional security tools aren't designed to detect.
For more on MCP security risks, see:
- Model Context Protocol (MCP): Landscape, Security Threat, and Future Research Directions
- MCP Security Checklist
MCP Security in Cortex Cloud WAAS
At Palo Alto Networks, we're committed to securing the technologies that drive innovation. Our new MCP Security capability in Cortex Cloud WAAS addresses the unique risks inherent to MCP communications. The feature provides two critical lines of defense.
1. Intelligent Protocol Validation
The WAAS protocol validation engine identifies and inspects MCP communications within general API traffic. It verifies structure against expected patterns, blocks manipulation of protocol elements, and stops injection attempts aimed at protocol parsing. While MCP allows for implementation flexibility, the engine adapts to legitimate variations and enforces consistency across requests.
2. API-Based Attack Prevention
WAAS also detects API-layer attacks targeting MCP endpoints. These include parameter tampering and other Layer 7 threats. Protections align with the OWASP API Security Top 10 to prevent misuse even when requests are well-formed.
Flexible Deployment Options
Understanding that organizations have diverse infrastructure requirements, WAAS module supports MCP security through multiple deployment methods:
API Gateway Integration
For organizations that use API gateways to manage traffic to their applications, MCP Security integrates directly with API gateways — including AWS API Gateway, Azure APIM, GCP Apigee, and Kong — without requiring changes to existing infrastructure.
XDR Agent for Cloud
For environments requiring real-time protection, our XDR Agent for Cloud offers WAAS capabilities with best-in-class runtime defense. This approach provides immediate security at the application level, preventing malicious requests before they reach MCP servers, as well as workload protection to prevent malicious exploitation.
The new MCP Security Detections are enabled as part of the “WAAS Advanced Threat Protection” capability.
Security Recommendations for MCP Builders
Teams adopting or building on MCP can reduce their risks by implementing these best practices:
- Use strong access controls: Apply least-privilege to every MCP tool and server
- Protect credentials: Avoid hardcoding credentials, rotate keys regularly, and isolate secrets
- Isolate runtime environments: Run MCP servers in isolated containers or sandboxed environments to prevent lateral movement if a server is compromised
- Enable detailed logging: Capture full MCP operations logs for anomaly detection
- Validate server identities: Ensure connections go to trusted MCP implementations
- Require confirmation for sensitive actions: Don't let the model act silently on risky requests
Comprehensive AI Protection: Beyond MCP Security
Securing MCP communications is imperative, but organizations need a holistic approach to AI security. Cortex Cloud offers additional capabilities that complement MCP Security to provide end-to-end protection for AI applications and infrastructure:
AI Security Posture Management (AI-SPM)
Cortex Cloud AI-SPM works alongside MCP Security to provide complete visibility and protection across your entire AI ecosystem, ensuring your teams can:
- Discover and inventory AI models deployed across your cloud environments.
- Assess AI-specific risks including data exposure, insecure model configurations, and vulnerable dependencies.
- Monitor the AI supply chain to identify poisoned datasets or unauthorized models.
- Enforce governance policies for responsible AI use and regulatory compliance.
- Detect misconfigurations in AI workflows that could lead to sensitive data exposure.
The combination of MCP Security and AI-SPM creates layers of defense, protecting how AI applications communicate via MCP and ensuring the underlying models, data, and infrastructure follow security best practices.
What This Means for AI Builders
The introduction of MCP Security in Cortex Cloud WAAS represents an impactful step in securing the future of AI applications. By validating MCP communications and preventing API-based attacks, organizations can:
- Deploy AI applications confidently: Implement MCP-based solutions with the assurance that communications are secured.
- Protect sensitive data: Prevent unauthorized access to resources and context information.
- Maintain model integrity: Ensure LLMs receive only legitimate requests and context.
- Enable secure innovation: Adopt new AI capabilities without compromising security.
MCP Security is available to Cortex Cloud WAAS customers at the end of May, 2025. Organizations interested in using MCP Security can contact their Palo Alto Networks representative.