Kubernetes doesn’t just orchestrate containers — it orchestrates complexity.
Security practitioners defending sprawling, multitenant environments can’t rely on surface-level dashboards or vague configuration alerts. They need a prioritized view of their Kubernetes security posture — one that moves beyond checklists and supports meaningful decisions.
That’s where Kubernetes security posture management (KSPM) comes in. Cortex Cloud introduces KSPM to help teams secure Kubernetes environments with industry-leading real-time protection, delivered by the only Code to Cloud to SOC security platform.
Cortex Cloud’s KSPM detects and remediates misconfigurations, vulnerabilities, malware and secrets across the software development lifecycle. With real-time protection enabled by a lightweight Kubernetes connector or cloud-based XDR agent, teams can stop threats before they escalate in production and secure workloads from code to cloud to SOC.
Today's blog post looks at Cortex Cloud’s KSPM capabilities, real-world workflows and best practices.
Know Your Inventory: Kubernetes Asset Visibility
Security begins with understanding your attack surface. In Kubernetes, that means full visibility into clusters, namespaces, nodes, workloads and the controllers that manage them.
Cortex Cloud’s KSPM Dashboard provides a live, interactive asset map across all clouds, enriched by agentless scanning and Kubernetes-native connectors. The dashboard invites deep exploration. Click the cluster count to see a breakdown of assets by platform — EKS, GKE, AKS, OpenShift. Hover over workloads to reveal ReplicaSets, DaemonSets, CronJobs and other components.
Every element is clickable, linking directly to a filtered asset inventory page. The ability to pivot from a broad overview to granular details in one click shortens the path from signal to insight, enabling teams to address asset sprawl, which can otherwise undermine Kubernetes environments.
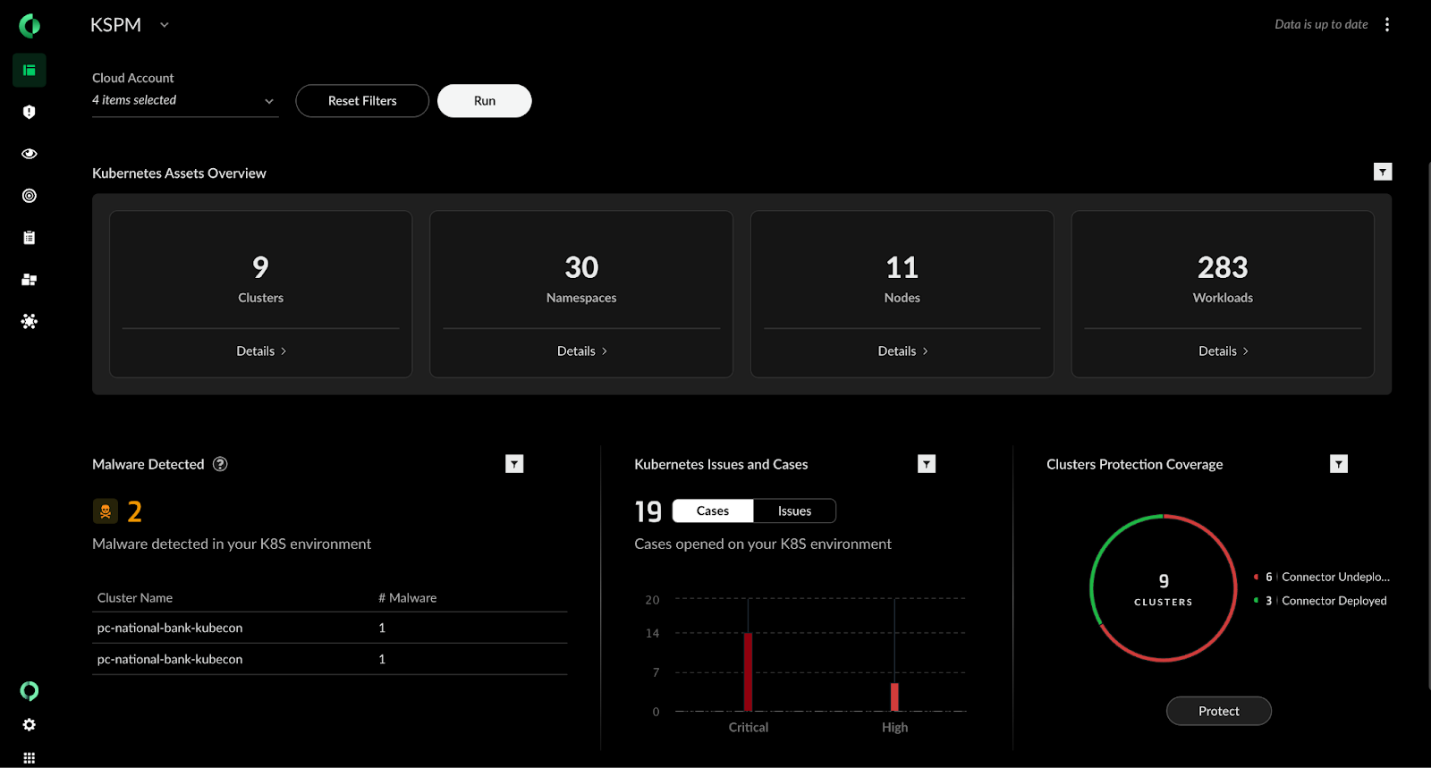
Kubernetes Security Insights
Security insights matter most when they’re prioritized, contextualized and actionable. The KSPM Dashboard aggregates findings across domains — including compliance, vulnerabilities, secrets and malware — to surface what deserves attention.
1. Riskiest Clusters
The Riskiest Clusters widget ranks clusters by a weighted risk score that factors in malware detections, compliance violations, vulnerability density and the presence of secrets. External exposure pushes a cluster to the top of the list. It’s a focused way to direct attention to what matters most.
Clicking a cluster opens its side card, complete with scores, issues and affected resources.
2. Top Clusters by Vulnerabilities
Not every CVE requires a response but clusters overloaded with critical and high-severity CVSS scores demand immediate review. Clicking a cluster opens a side panel with asset ID, cloud region, tags, asset group and associated findings. Use “Resource Explorer” to access a full inventory of affected assets, sorted and ready for triage.
3. Secrets Detected in Clusters
Leaked secrets break trust, and this widget helps teams find them before anyone else does by categorizing and counting secrets. Clicking a secret type reveals the implicated clusters harboring plaintext, hard-coded credentials and/or misconfigured encryption keys.
4. Malware Detected
Clusters compromised by known malware appear in a sorted view based on malware volume. Side cards show affected assets and provide guidance for response. When malware hits, speed matters. Cortex Cloud helps cut through noise and move fast to containment.
Built for Security Team Workflows
KSPM isn’t just powerful because of what it shows — it’s how teams use it. Investigation doesn’t require jumping between tools. Each widget supports intuitive workflows: side-card previews for single assets, detailed list views for asset groups and direct action links for fast response.
To narrow the focus by cloud account or asset group, apply a single filter and watch the entire view update. Settings are persistent — preferences stay in place across sessions.
The dashboard is export-ready. Whether preparing for a report or an audit, the data’s ready to go. Role-based access control (RBAC) is enforced throughout the dashboard interface. Only users with edit rights see control options.
KSPM Best Practices for Practitioners
Integrate KSPM into a Container Security Strategy
Use KSPM as part of a broader container security approach to ensure full coverage across the container lifecycle — from code to cloud. This integration helps identify and mitigate risks at each stage, including code, build, deploy, and runtime.
Continuously Monitor Your Kubernetes Environment
Monitor clusters using agentless scanning, the lightweight Kubernetes connector and the Cortex XDR® agent for cloud. These tools provide real-time visibility into misconfigurations, vulnerabilities, secrets, malware and compliance issues. Continuous assessments support proactive remediation and preserve a strong security posture.
Maintain Up-to-Date KSPM Rules and Policies
Keep KSPM rules and policies current to enforce compliance and identify posture violations. Set up guardrails to block deployments that violate cloud workload policies. Regular updates ensure your environment stays aligned with the latest protections.
Prioritize Risks Identified by KSPM Scans
Focus on the riskiest clusters first — those with critical vulnerabilities, malware, exposed secrets or misconfigurations. Prioritization drives efficient use of resources and strengthens cluster defenses.
Implement Role-Based Access Control
Apply RBAC to enforce least privilege across your Kubernetes environment. Access controls reduce the risk of unauthorized activity and limit attack surfaces.
Operationalizing KSPM with Cortex Cloud
Kubernetes security posture management isn’t a set-it-and-forget-it task. It’s an ongoing discipline of monitoring environments, enforcing policy and auditing configurations.
Cortex Cloud’s KSPM capabilities strengthen Kubernetes security by surfacing what matters and giving practitioners the tools to act with speed and precision.
We enable DevOps, platform engineering and security teams to drive security outcomes — without slowing innovation.
But why take our word for it when you can sign up for a free trial and experience Cortex Cloud KSPM first-hand.