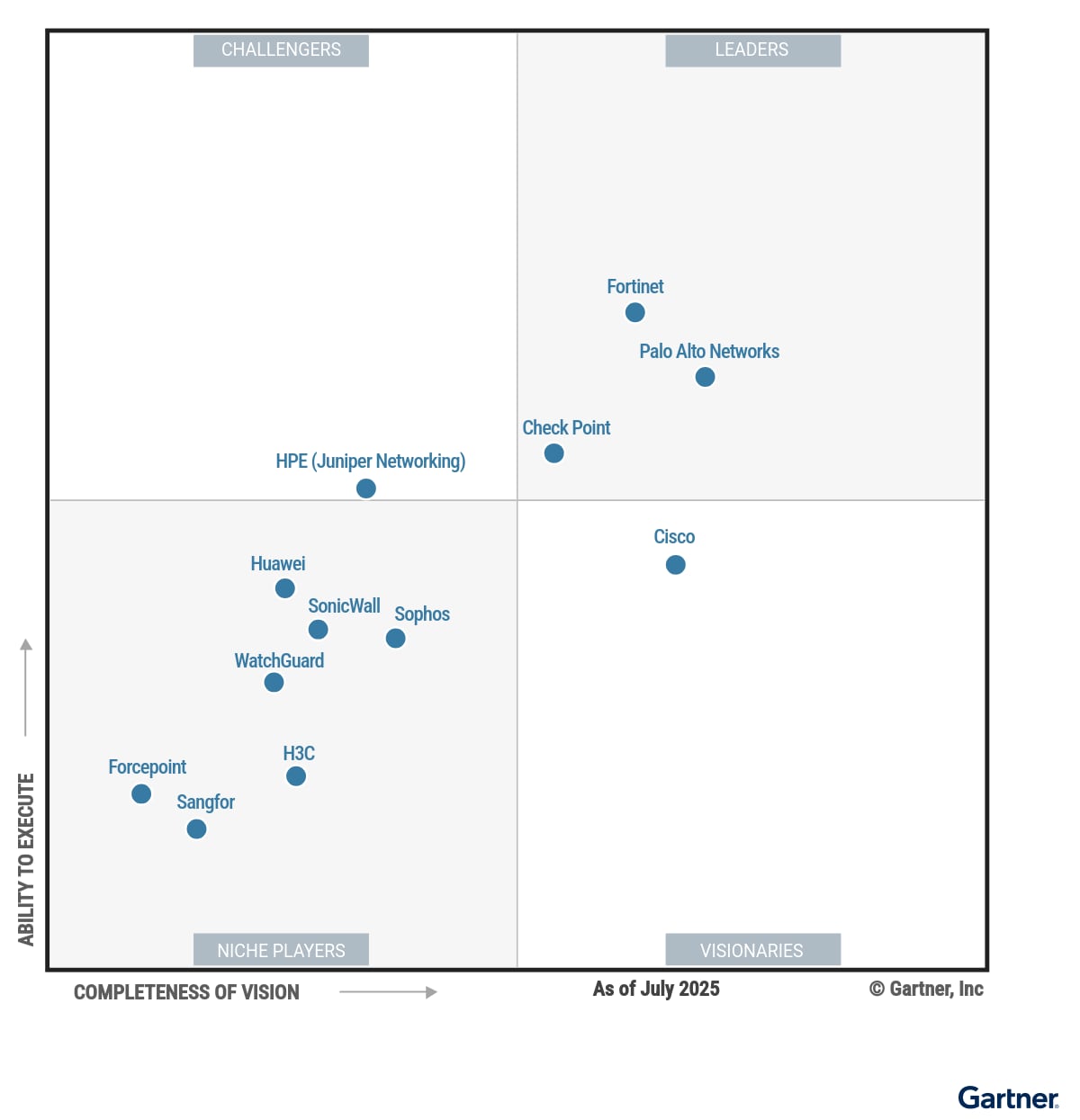
Palo Alto Networks has been named a Leader in the 2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewalls, recognition we believe reflects the expanded mandate of the modern firewall to secure users, workloads, and connected devices across today’s enterprise.
Firewalls have long been central to protecting users, applications, and workloads. Today enterprises rely equally on connected devices, and security platforms must deliver visibility and protection for those devices natively.
We believe this recognition highlights a broader market shift toward integrating IoT and OT protections into unified security platforms rather than managing them through separate point products. We have always delivered these protections natively through NGFW and SASE. Building on that foundation, we have recently introduced our Device Security solution, which expands protections beyond IoT and OT to provide comprehensive security across all connected devices, managed or unmanaged.
As defined in the Gartner 2025 report, a hybrid mesh firewall is:
A hybrid mesh firewall (HMF) is a multideployment firewall model that spans hardware, virtual appliances and cloud-based options, all managed through a unified, cloud-based management plane. HMFs are designed to support hybrid environments and evolving use cases by integrating seamlessly with CI/CD pipelines, enabling native cloud controls and providing advanced threat prevention against challenges, such as IoT risks and DNS-based attacks.
We believe this aligns closely with what we see in the market—enterprises not only need integrated security capabilities and strong prevention, but also require these to extend across IoT and OT devices that underpin business operations.
Comprehensive Visibility and Policy Control
For many organizations, even the basic question of what devices are connected to the network does not have a reliable answer. Devices often appear faster than they can be inventoried, many are unmanaged or unpatched, and traditional controls rarely provide complete visibility. Blind spots quickly translate into risk.
Our hybrid mesh firewall, as part of a unified platform, helps address this challenge by discovering devices that communicate through it and enriching that view with context. Teams can see device identity and risk posture, understand how exposed a device is within the network, and know what security coverage is already in place — all within a single view.
Beyond visibility, each device is continuously evaluated against expected behaviors and posture baselines, enabling security teams to move from insight to action in real time. Policies can adapt dynamically to a device’s identity and risk context, supporting segmentation that limits communication to only what is required, guided virtual patching for vulnerabilities that cannot be addressed through updates, and enforcement that responds if behavior changes unexpectedly.
This combination of visibility and control within a single platform helps reduce complexity and gives security teams greater confidence in protecting their environments.
Continuous Inspection and Adaptive Protection
Protecting connected devices requires more than visibility — it demands continuous inspection to detect and prevent malicious activity before it causes damage. Attackers target weak configurations, missing patches, and default credentials, and traditional controls often fail to catch those threats in time.
Our hybrid mesh firewall delivers continuous multilayered security inspections and protection through integrated security services. It blocks exploits, malware, spyware, and command-and-control traffic in real time. AI-driven anomaly detection establishes baselines for how devices normally behave and immediately flags deviations. In industrial environments, OT-aware inspection helps preserve process integrity by stopping unauthorized or unsafe commands at the protocol level.
These capabilities provide adaptive protection that responds as risks evolve, building on the context established through device discovery and posture assessment. Vulnerabilities that cannot be patched directly can be mitigated through guided virtual patching, reducing exposure without disrupting operations.
Security at Scale
Protecting connected devices is not only a visibility or prevention challenge; it is also a security challenge. It is also an operational one. Using multiple siloed tools increases complexity, creates gaps, and raises costs.
With Palo Alto Networks, customers gain a platform approach that consolidates visibility, prevention, and control into one place. Device context spans posture, network exposure, and security coverage. Policies adapt dynamically to evolving device behavior, and protections are enforced consistently across network, cloud, and branch environments. Deployment is straightforward, and meaningful visibility can be achieved quickly without requiring additional hardware.
This approach helps organizations extend protection across millions of devices while simplifying operations and maintaining consistency at scale.
Securing the Enterprise of Connected Devices
Enterprises today are defined as much by their devices as by their users and workloads. Firewalls must reflect that reality. The mandate has expanded from guarding the perimeter to protecting the full fabric of the enterprise, including the connected devices that keep it running.
We believe our recognition as a Leader in the 2025 Gartner Magic Quadrant for Hybrid Mesh Firewalls reflects our vision that enterprises need security platforms built to protect not only users and workloads, but also the connected devices that keep business running.
Explore how we protect every device—managed, unmanaged, and IoT. See why Gartner named us a Leader in hybrid mesh firewalls.
Gartner Disclaimer
Gartner, Magic Quadrant for Hybrid Mesh Firewall, Rajpreet Kaur, Adam Hils, Charanpal Bhogal, Esraa EITahawy, Feng Geo, Tiffany Taylor, 25 August 2025
GARTNER is a registered trademark and service mark of Gartner and Magic Quadrant is a registered trademark of Gartner, Inc. and/or its affiliates in the U.S and internationally, and are used herein with permission. All rights reserved. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Palo Alto Networks.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.