Research by: Matan Haim Guez, Tom Fakterman, Yoav Zemah
Executive Summary
One of the key phases of a cyberattack lifecycle is the persistence phase. In its essence, persistence deals with maintaining a foothold in a compromised system, usually by setting up an automatic execution of malicious code on system startup, user login, or upon specific system events. Nowadays, there are dozens of documented persistence techniques which are actively being used by threat actors in the wild.
Given its criticality, variation, and its tendency to occur in the earlier stages of an attack, the persistence phase poses great challenges for defenders who wish to detect and prevent an attack as early as possible. The daunting task of tracking different persistence mechanisms one by one can lead to many false negatives (FN). In addition, trying to keep track of each new method or detection bypass technique is often futile and can be likened to a game of “whack-a-mole”.
To face this challenge, the Palo Alto Networks Cortex Research Team developed a unique suite of detection modules titled “Generic Persistence Analytics”. This module leverages unique insights derived from our machine learning (ML) and analytics engine that can detect the execution of malicious files, during the persistence phase - regardless of the technique that was used to achieve it.
In this writeup we will dive into the technical details of this unique data-driven approach. We will also provide real-life use cases demonstrating the persistence detection by the Generic Persistence Analytics module.
Table of Contents
Windows Malware Persistence in a Nutshell
Different Persistence Techniques
Current Persistence Detection Approach and Challenges
The Generic Persistence Analytics Suite
The Rational of Examining Parent Processes
Statistic-Based & Machine Learning Detection Capabilities
Cyber Features: Diving into Details
Windows Malware Persistence in a Nutshell
In the attack lifecycle, persistence is considered a key stage in maintaining a foothold in a compromised environment. Persistence is the repeated execution of a program under a predetermined condition, dependent on the operating system.
In Windows user mode, there are several known persistence mechanisms, such as registry AutoRuns keys, scheduled tasks, and system services. In kernel mode, there are low-level components such as drivers, which get loaded and executed by the kernel in an early stage of the boot process and can be used as a persistence mechanism as well.
The variety of different persistence methods assists in concealing the root cause of a given malware's execution. Moreover, malware can escalate its privileges through the malicious use of a mechanism's features. For example, an attacker can create a new scheduled task on a compromised machine and set up the task to execute their malicious payload with administrator privileges.
Different Persistence Techniques
Below are examples of common persistence mechanisms, representing only the tip of the iceberg in terms of persistence mechanisms used in the wild:
- Scheduled Tasks: This Windows system feature allows users to automate tasks by setting them to execute periodically at certain times or upon certain events. It can be configured to execute potentially malicious scripts, applications, or even administrative tasks without requiring user intervention.
- Registry autorun keys and startup folders: Registry AutoRun keys allow attackers to add entries to the Windows registry and run malicious code automatically at startup or user login. Similar to registry autorun entries, attackers may simply place a shortcut to malware in a Windows startup folder to ensure its execution upon user login.
- Bootkits: These are sophisticated types of malware that infect a computer's boot process, allowing it to run before the operating system starts. Bootkits can obtain low-level system control by compromising the boot procedure, making them exceedingly difficult to detect and uninstall. Because of that, bootkits are an effective weapon of choice for attackers seeking to achieve long-term and stealthy persistence on a target’s machine. This is usually done by infecting the MBR (Master boot record) or the Unified Extensible Firmware Interface (UEFI).
- Winlogon registry key: Winlogon is an essential Windows operating system component that manages user logins and other session-related actions. Attackers can modify the registry values Shell, Userinit, and Notify in Winlogon registry keys to point at a malicious executable or a script that runs instead of (or alongside) explorer.exe and userinit.exe to establish persistence in an early startup stage.
- WMI: (Windows Management Instrumentation) is a framework that allows scripts and applications to manage devices, services, and processes in a Windows environment. WMI event subscriptions are a powerful mechanism that can be abused for persistence by allowing an attacker to automatically trigger malicious actions based on specific system events.
An attacker can create a persistent WMI subscription by defining an event filter that triggers certain system events (e.g., at system boot or user login) and linking it to a malicious script or executable.
Current Persistence Detection Approach and Challenges
Upon conducting our research, we concluded that the current approach in the cybersecurity industry for detecting malicious persistence is to observe and detect the action of setting up the various known persistence mechanisms. For example, when detecting registry persistence, vendors will look for a process that sets a value in the registry in one of the known AutoRun keys.
There are multiple issues with this approach:
- Legitimate products and applications also use persistence as a feature, making it hard to discern between a legitimate persistence or malware-generated persistence - thus resulting in an extensive number of false positive (FP) alerts that do not necessarily indicate malicious activity.
- The aforementioned detection approach, coupled with the variety of built-in mechanisms in Windows, encourages security vendors to create more ad-hoc detections over time.
- If one specific detector fails, it will be far more difficult to determine the persistence mechanism for malware launched at startup or login and will necessitate a more challenging in-depth investigation of the artifacts from the affected machine.
- If the infection employs a new persistence technique that security vendors are unaware of, no alert will be delivered, making it far more difficult to identify the malware's initial persistence technique and completely mitigate the compromised machine.
The wide range of persistence techniques yet limited detection approaches have created a problem for all security products and vendors, diminishing the ability to detect different & new persistence methods.
The Generic Persistence Analytics Suite
The Cortex XDR research team chose to handle the problem of detecting malicious persistence using a novel approach that required us to step back from the common detection-by-technique method and embrace what we call “The Concept of Generalization”, using our set of detectors now known as the “Generic Persistence Analytics”.
The new detection suite detects startup persistence techniques which are frequently employed in malware in the wild, while focusing on the execution stage, where a malicious payload is executed by a persistence mechanism.
The Concept of Generalization
In the context of detecting malicious persistence activity, generalization refers to a detection mechanism’s capacity to effectively detect a wide range of malicious persistence techniques, even unknown techniques that have yet to be reported.
It guarantees that the detection mechanism is effective against a wide range of threats, not only those already detected and known.
In practice, this means that we utilized Generic Persistence Analytics to detect the majority of malicious startup persistence without adding additional technique-specific detections. A diagram that represents the difference in the generic and existing approaches of persistence detection on the market can be seen in Figure 1.
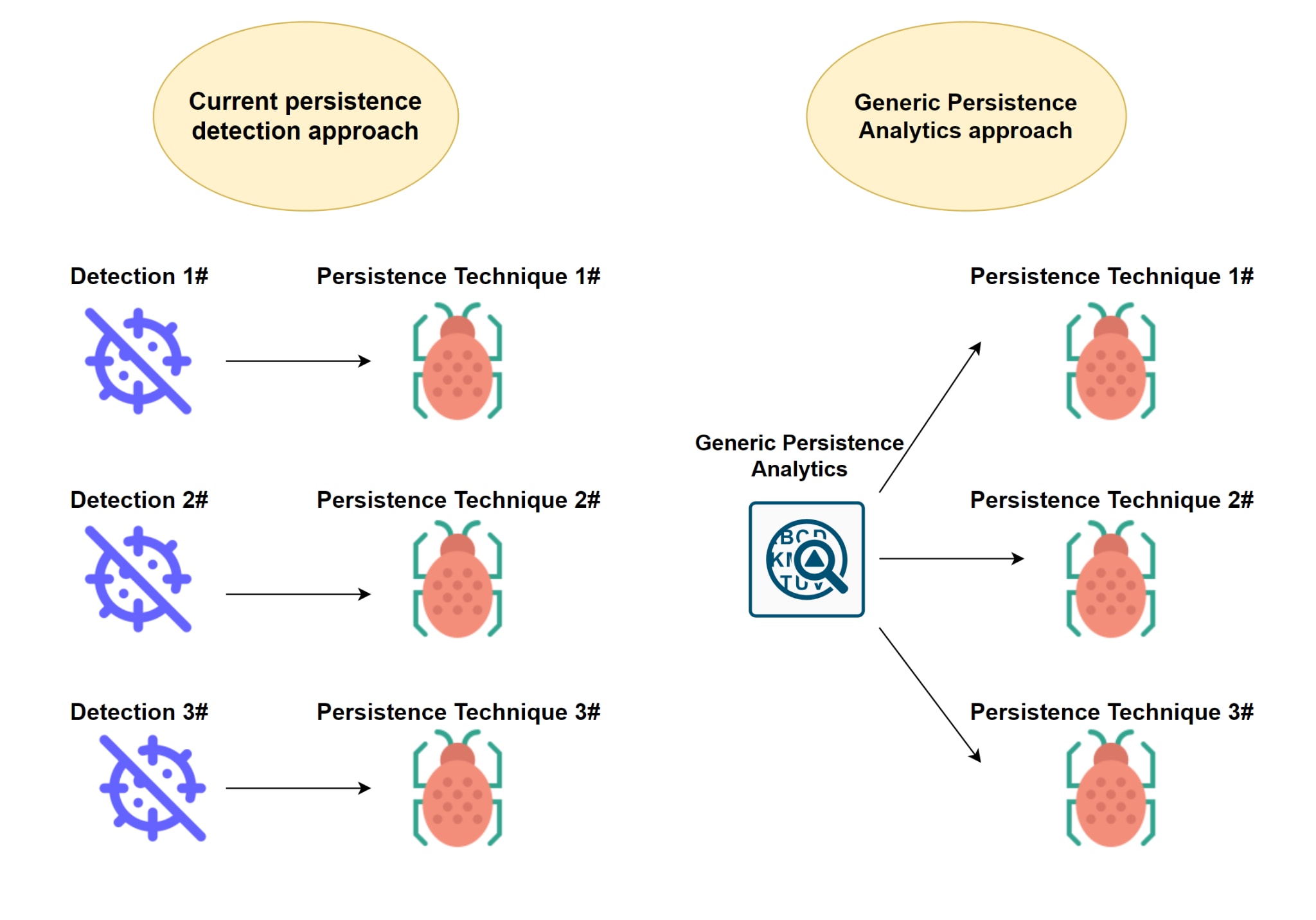
Implementation
To solve the persistence detection problem in a generic way, we needed to focus on one thing that almost all persistence mechanisms have in common: They all eventually execute a process, and as was mentioned before, we focus on process execution in an early startup stage, while persistence is triggered on startup.
With this in mind, we began our solution implementation by collecting all process execution events at startup. However, in order to establish an efficient and precise detection, we needed to continue researching data that was collected from those process execution events.
Statistic-Based and Machine Learning Detection Capabilities
In order to create statistics-based detection while collecting all process execution events at launch, we used Cortex Analytics. The Cortex Analytics Engine generates aggregations based on real-time events from Cortex agents. These aggregations are then utilized to construct baselines of common behaviors globally, for each organization, and for every agent. Then, the detector asks the necessary questions to decide with certainty whether an action is usual or unusual for every event. These questions direct us to the main objects we should aggregate and the relationships between them, such as:
- How popular is the process in the organization?
- How popular is the execution of a process by a specific persistence mechanism?
- How many days have we seen this process executed on startup in the organization?
As with every detection, there is a delicate balance of FPs and FNs. We may filter out FPs by asking the aforementioned statistics-based questions and more.
By providing Generic Persistence Analytics with such power, we can successfully address an existing problem that was a real pain for persistence detection.
The Rational of Related Entities
When collecting different process execution events on startup, it is important to note that all of these collected events have the potential to be malicious persistence events. To determine which process execution was malicious, we needed to investigate all processes engaged in spawning child processes during the boot procedure.
During our research of processes that were executed at an early startup stage of the operating system’s boot time, we discovered that we can determine the persistence mechanism for the majority of known persistence techniques. We can direct affected organizations to the corresponding persistence mechanism used for a specific malicious activity. Figure 2 below depicts the different alerts raised by the two different approaches, the current and generic.
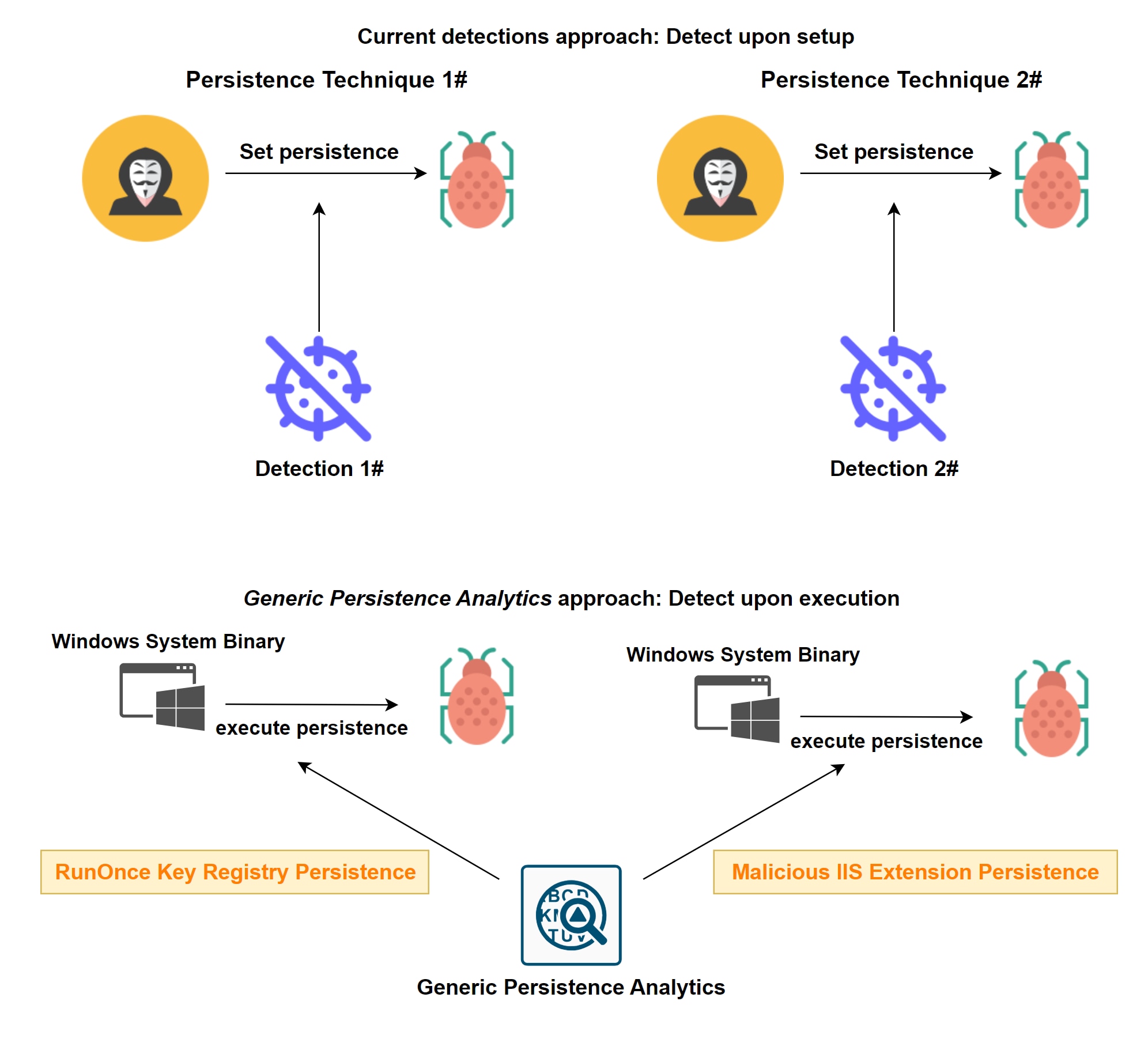
Cyber Features: Diving into Details
Cortex XDR Analytics is a data-driven detection engine that collects both behavioral and static information in order to raise suspicion on certain process images in addition to executed processes.
To create the Generic Persistence Analytics, we collected data features from Portable Executable (PE) files and compared them to a number of conditions.
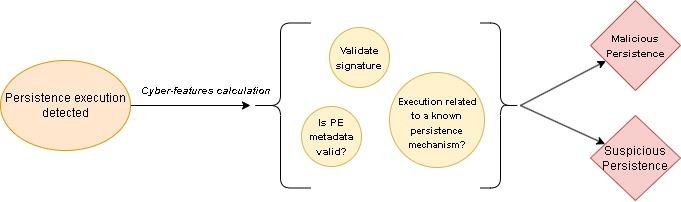
We were able to identify aspects of a PE file that, along with other features, assisted in flagging processes as malicious. Some of those features include:
- Signature status: The validity of the signature, rarity in the organization, etc.
- PE metadata: has it been modified?
- Was the process’s execution a part of a known persistence mechanism?
The above list is just a part of the capabilities of Cortex XDR Analytics. When we combined these features with statistics-based and machine-learning detection, we achieved incredible precision and efficiency. Figure 3 depicts these features we call “Cyber-features” that answer the above questions upon process execution.
Persistence in the wild
The following section provides real-life cases found in our telemetry, showcasing various malware that use different persistence techniques - and are all caught by the Generic Persistence Analytics module, agnostically to their persistence technique that was implemented.
Glupteba
Glupteba is an advanced modular malware that is mostly used in financially driven cybercrime operations. In February 2024, Unit 42 researchers analyzed Glupteba’s previously undocumented feature - a UEFI bootkit.
Glupteba features multiple different downloadable modules at its disposal.
These modules give the malware the following capabilities:
- Delivering additional payloads.
- Stealing credentials from various software.
- Stealing sensitive information, including credit card data.
- Enrolling the infected system in a crypto-mining botnet.
- Cryptojacking and delivering cryptominers.
- Performing digital advertising fraud.
- Stealing Google account information.
- Bypassing User Access Control (UAC) together with both rootkit and bootkit components.
- Exploiting routers to gain credentials and remote administrative access.
In order to achieve persistence, Glupteba uses an open-source and portable UEFI bootkit named EfiGuard. EfiGuard patches the Windows kernel by executing a UEFI driver (EfiGuardDxe.efi) to disable PatchGuard and driver signature enforcement (DSE). Additional analysis of Glubteba’s UEFI bootkit process is detailed in the aforementioned Unit42 analysis.
Figure 4 shows Glubteba’s execution after a reboot of the infected machine
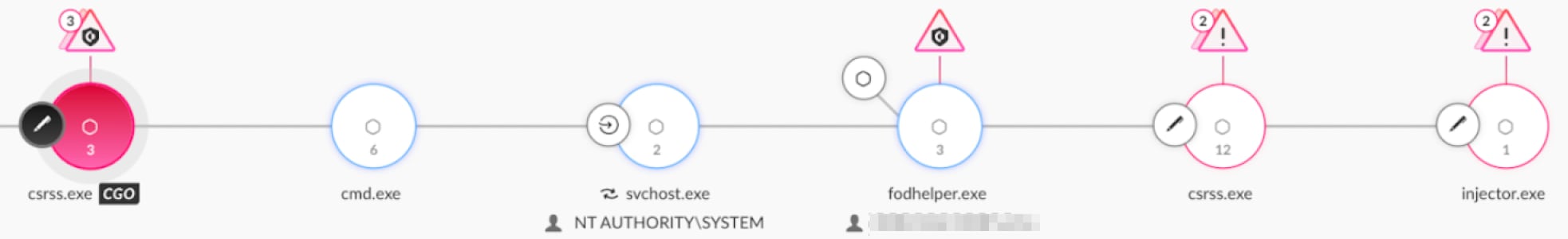
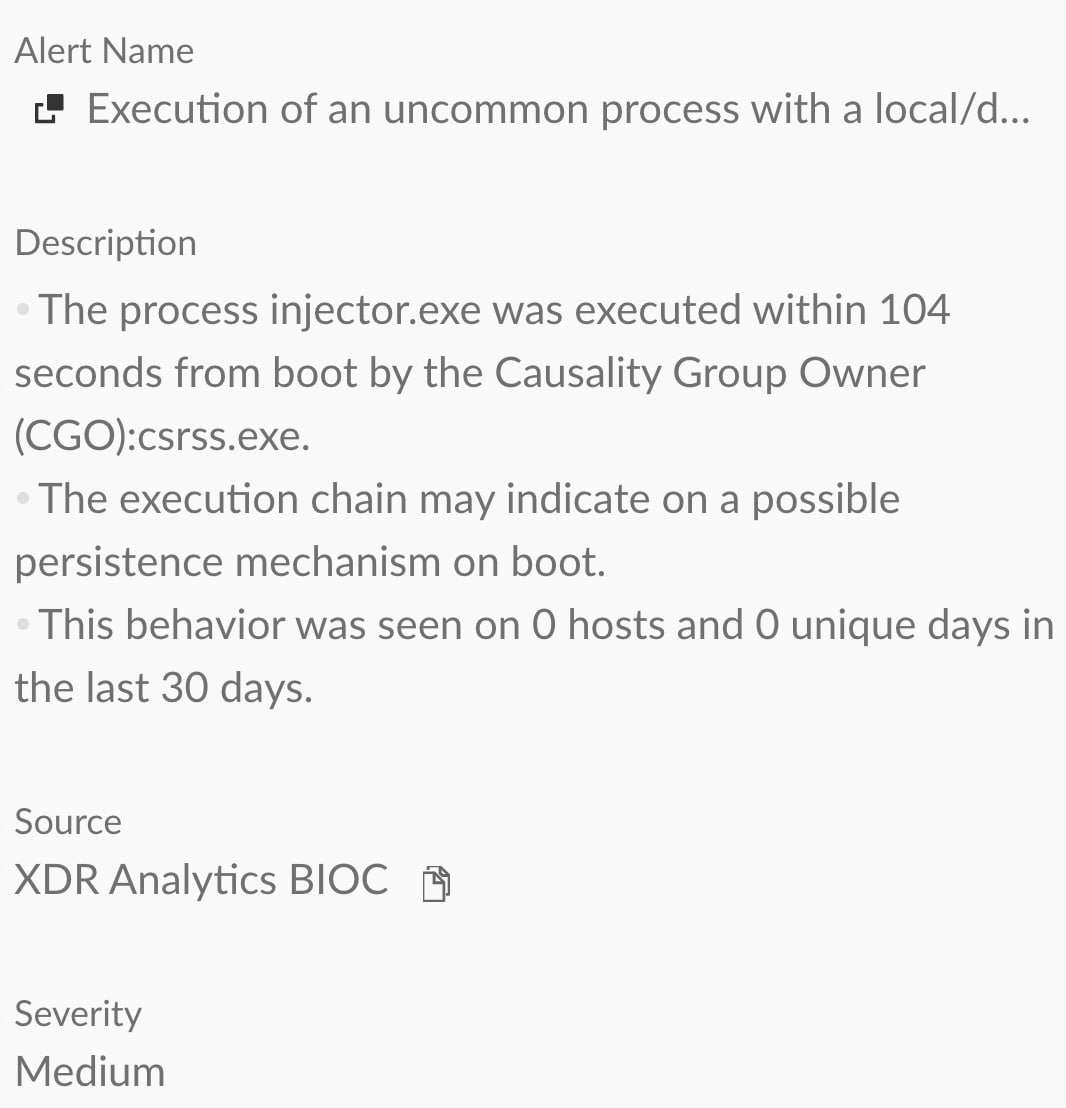
Cortex XDR detects and prevents Glubteba’s persistence mechanism. Figure 6 and Figure 7 show the Cortex XDR alert for Glupteba’s detected persistence.
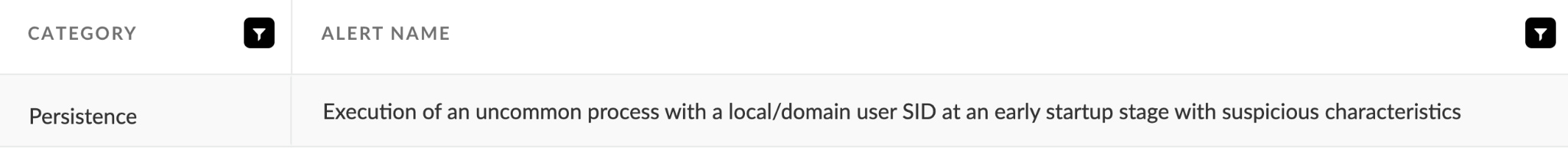
Figure 6. Alert title for Glubteba’s persistence in Cortex XDR.
XWorm
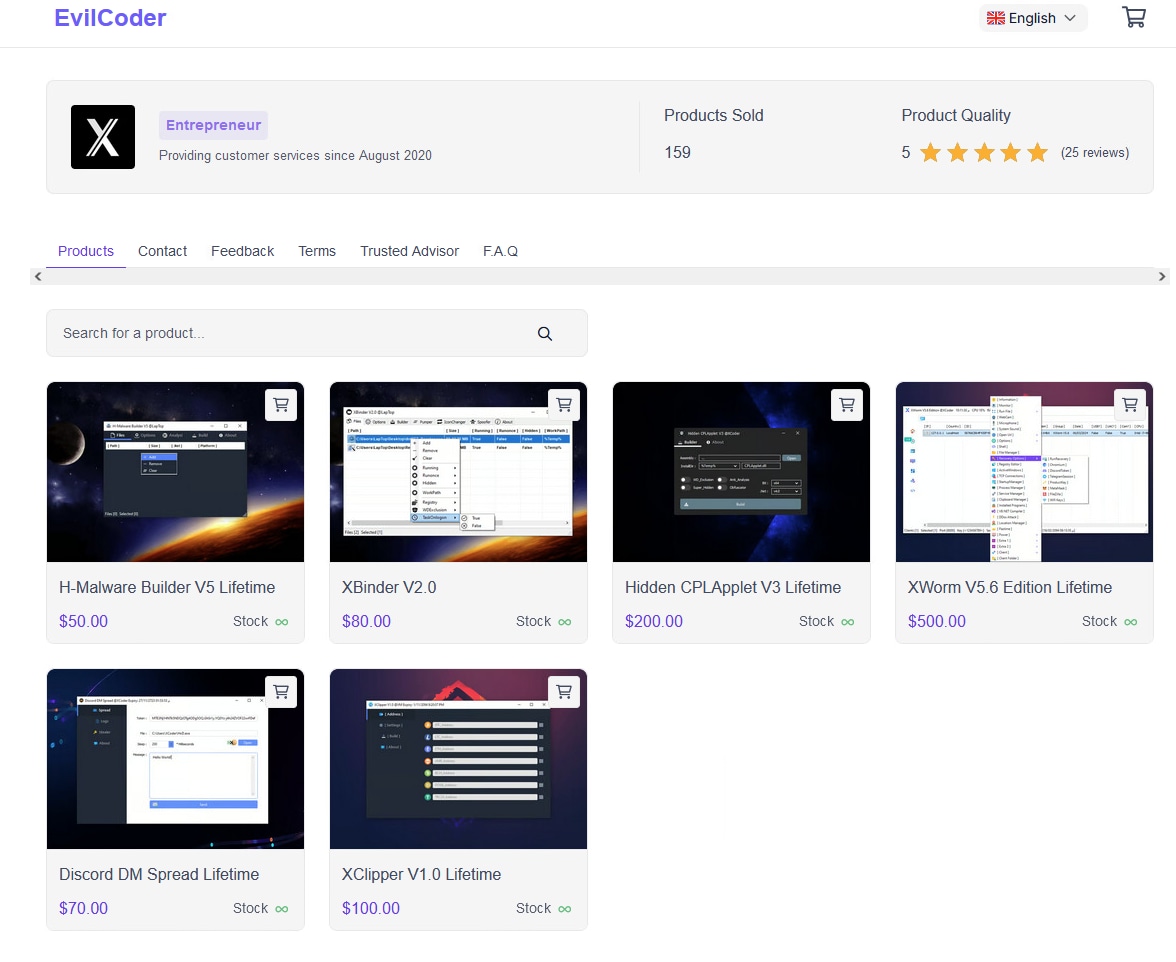
XWorm is a Windows remote access trojan (RAT) written in .NET, and sold online in popular hacking forums and different underground marketplaces under the user aliases “XCoder” or “EvilCoder”. Figure 8 shows an online marketplace that sells XWorm.
The XWorm RAT has many different typical remote administration capabilities and features, including:
- Keylogging and window monitoring.
- Process and script execution.
- Monitor webcams and microphones.
- File system interaction.
- Upload and download files.
- Interactive shell.
- Password stealing.
- Ransomware.
- Distributed denial-of-service (DDoS) attack.
When examining XWorm’s persistence mechanism, we noticed that it is capable of using several common techniques depending on the malware’s configuration:
- Creating a scheduled task.
- Registry autorun keys.
- Placing a copy of itself in the Windows startup folder.
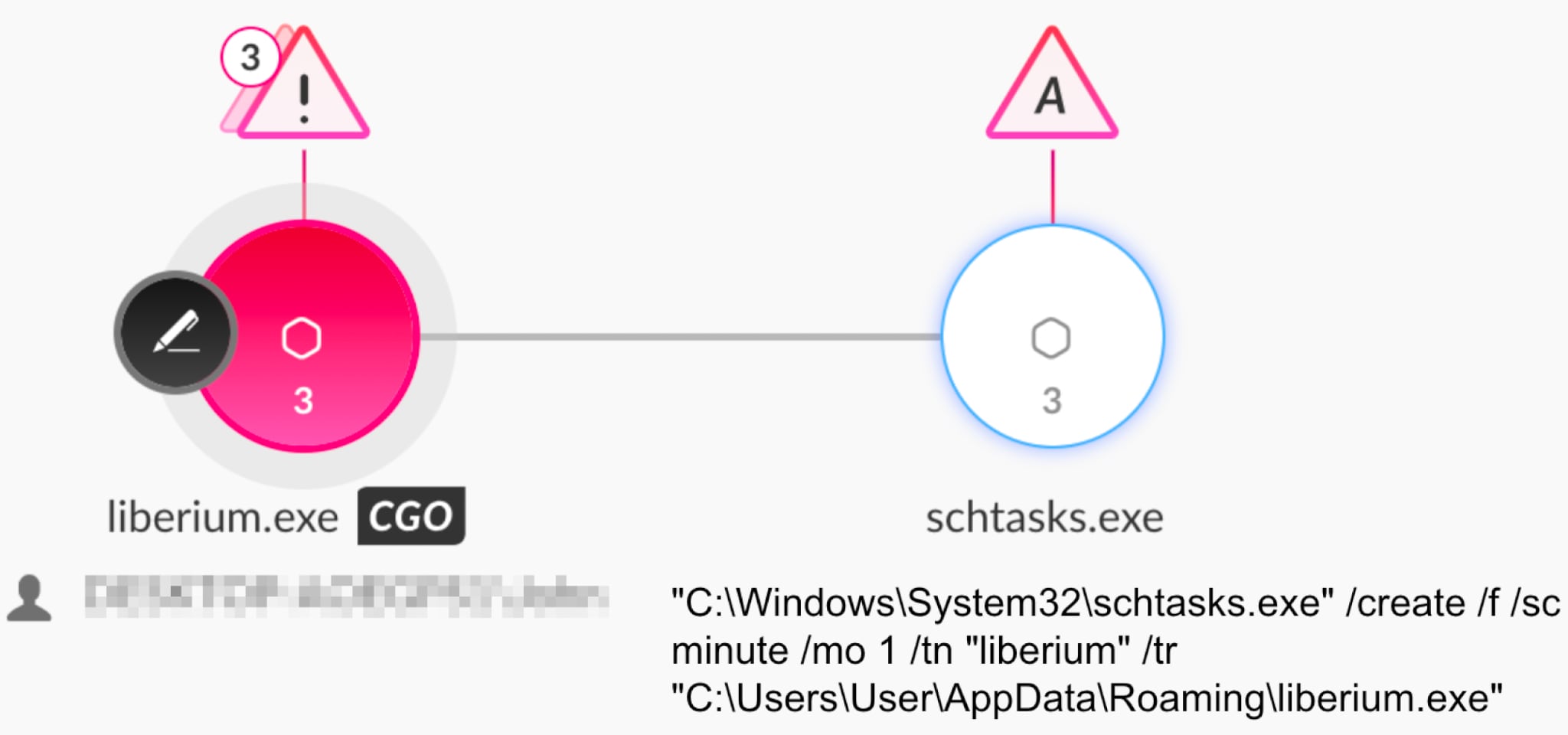
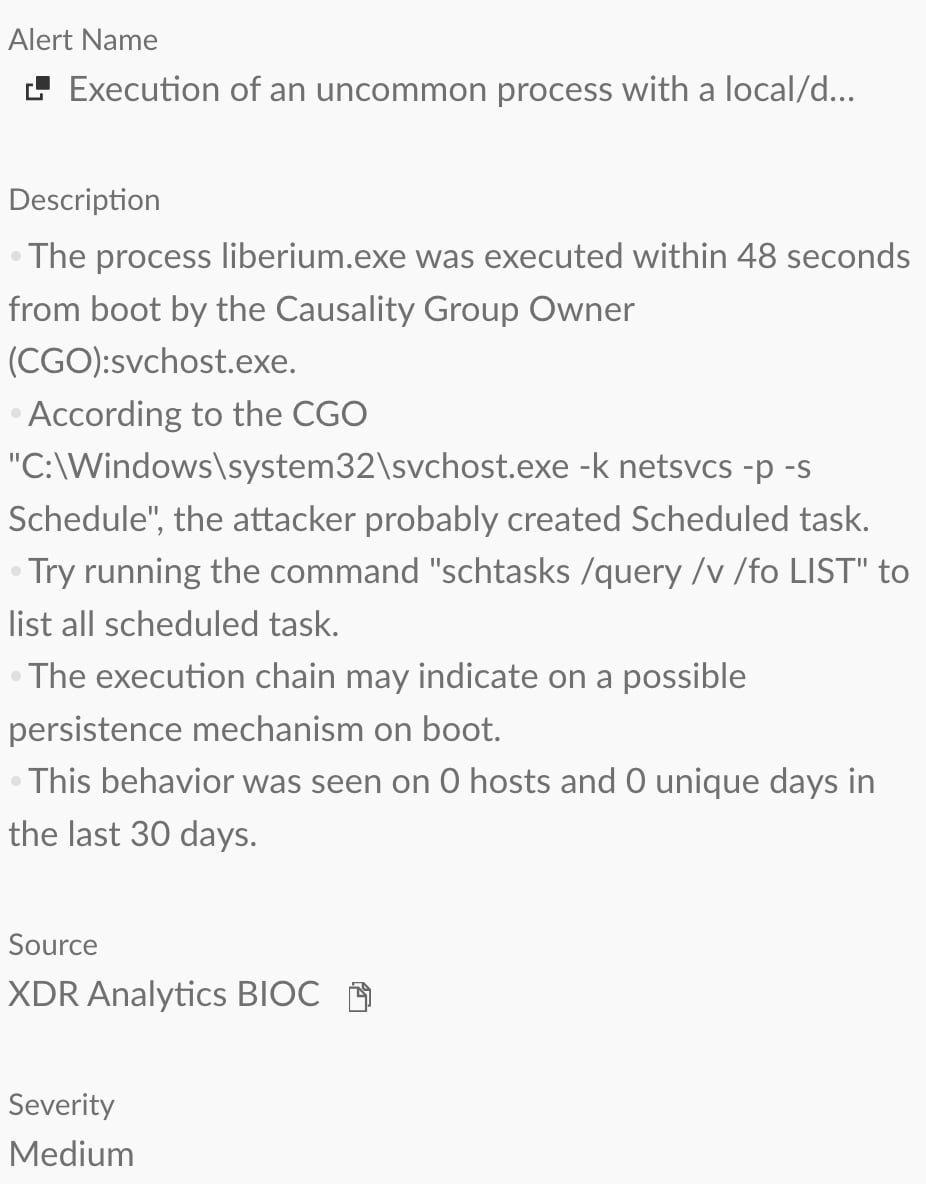
The Cortex XDR Generic Persistence Analytics suite detects and prevents XWorm’s aforementioned persistence mechanisms using its unique approach.
Figure 9 and figure 10 show the execution and detection of a scheduled task created by XWorm as seen in Cortex XDR.
Agent Tesla
Agent Tesla is a Windows information stealer written in .NET that has been active since at least 2014. It is sold on the dark web and primarily distributed through phishing emails.
Agent Tesla's capabilities are extensive, and its builder allows attackers to use a variety of configurations, enabling them to craft variants with different capabilities upon each compilation. The primary capabilities of Agent Tesla include:
- Stealing Sensitive Information:
Agent Tesla can extract sensitive information stored on an infected device. It is particularly effective at stealing credentials, including those stored in web browsers (such as passwords, cookies, and autofill data), FTP clients (like FileZilla), and VPN clients (such as OpenVPN). - Keylogging:
Another significant capability of Agent Tesla is its keylogging functionality. It can capture every keystroke of the user, including typed passwords, messages, and any other input. - Taking Screenshots:
Agent Tesla can periodically capture screenshots of the victim's desktop. This feature can capture sensitive information that might be displayed on the screen, such as private messages, documents, or images.
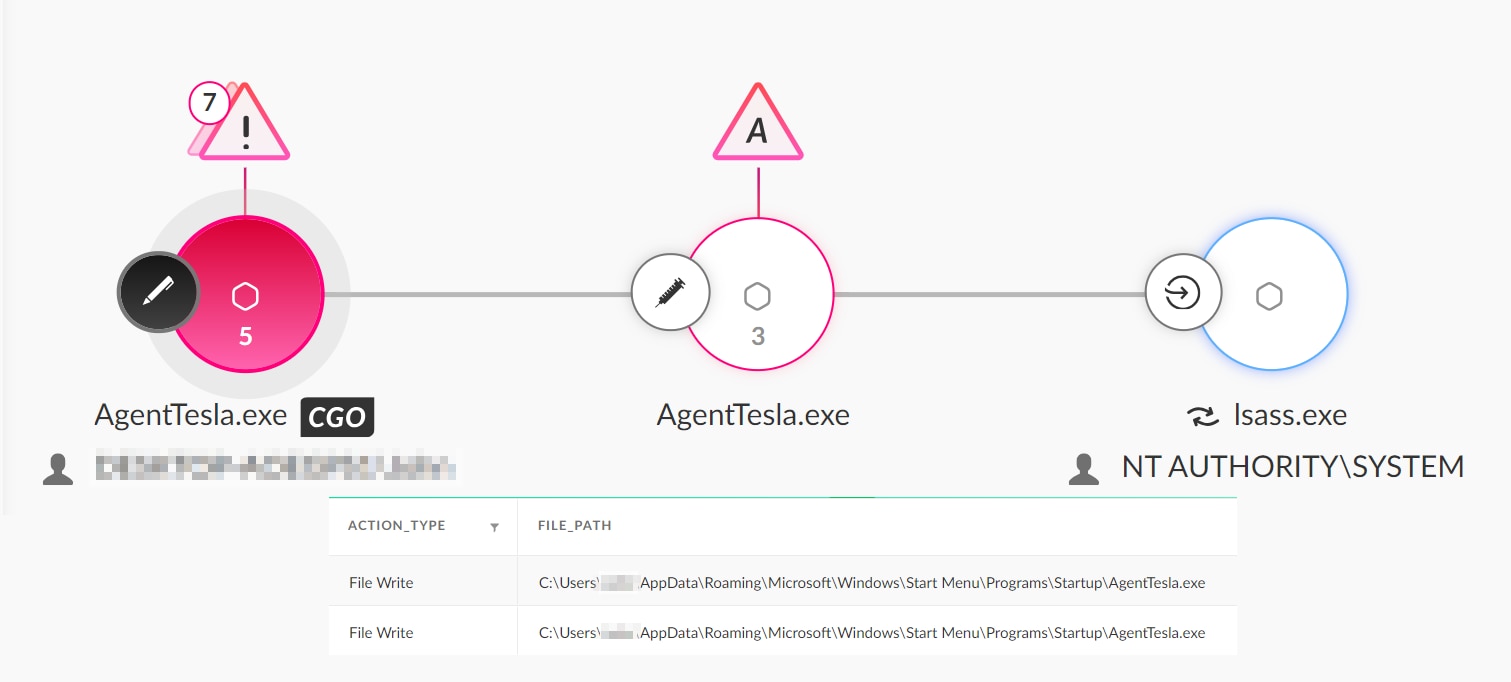
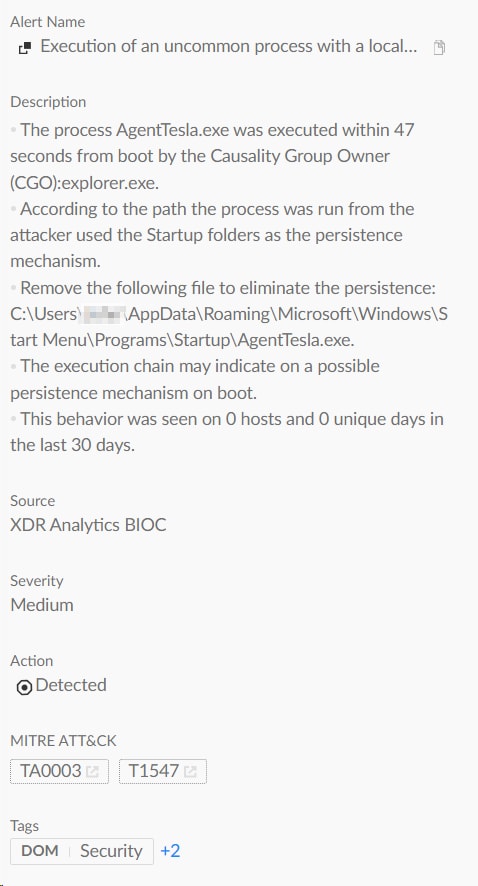
Agent Tesla can achieve persistence using various techniques, such as adding itself to the startup folder, thus ensuring it runs every time the infected system boots up, creating scheduled tasks, and modifying registry keys. Figures 11 and 12 illustrate the execution and detection of AgentTesla adding a copy of itself to the Windows startup folder, as observed in Cortex XDR.
Conclusion
In this writeup, we introduced the novel Cortex Generic Persistence Analytics detection suite. We demonstrated how the Generic Persistence Analytics suite, built on the Cortex Analytics engine technology, provides a substantial breakthrough in the detection of both known and previously undisclosed persistence techniques, using a novel statistical-based approach.
We reviewed common persistence mechanisms and demonstrated real life use-case scenarios and the detection of how the Cortex Generic Persistence Analytics suite detects and prevents these advanced threats, ranging from RATs to bootkits.
By harnessing the power of machine learning and statistical-based methodologies with substantial cyber security expertise, the Cortex Analytics research team was able to create a comprehensive approach that meets the complicated nature of the ever-evolving threat landscape, raising the bar of endpoint protection once again.