Palo Alto Networks Unit 42 Managed Services team delivered outstanding results in the face of MITRE Engenuity’s first-ever ATT&CK® Evaluations for managed services. Our elite security experts at Unit 42 delivered a comprehensive threat report that provided quick and accurate attribution of the adversary and the tactics they used to accomplish their malicious objectives. As the attack progressed, we quickly identified patterns of behavior that indicated one of the dozens of adversaries with which we are intimately familiar, and the threat report we delivered accurately attributed the attack to APT 34, also known by the handle, OilRig, a name we gave them back in 2016 when we published the first research on this adversary. (For more information, read about our Unit 42 backstory and our research on OilRig).
With the overwhelming growth in cybercrime, businesses are turning to managed service providers to help protect and recover from cyberattacks. Choosing the right provider has been challenging as there is little information about how to compare the services and value they provide. Helping businesses choose the right provider for them was the goal of this first MITRE Engenuity ATT&CK Evaluations for Managed Services. As a consistent participant in the Enterprise Evaluations, Palo Alto Networks was invited to participate, and our Unit 42 Managed Services team was eager to put our methodology on display.
Unlike previous evaluations, this would be a closed-book process, where the adversary, time of the attack, and tactics and techniques would not be revealed until after the attack scenario was completed. The focus of this go-round was on the quality of the post-breach threat report that the service provider would deliver. It's worth noting that MITRE Engenuity (ME) requested that vendors configure their defenses in detect-only mode, with no prevention enabled.
When your organization is responding to a breach scenario, time is critical. The longer an adversary has access to your infrastructure, the more damage they can do to you. We recommend you try to answer the following questions quickly:
- What is the impact?
- Who is attacking you?
- What is their objective?
- Which TTPs did they use?
- How should you respond?
The threat reports delivered by your service provider should help you get to these answers as quickly and efficiently as possible. Often, threat reports contain too much information, burying the critical information CISOs and security teams need to make quick decisions while ensuring their response completely eradicates the adversary and fully remediates any actions they have taken.
Our Results
In this evaluation, our Unit 42 MDR service delivered a threat report which accurately and succinctly identified all of the key information needed to mount a complete response. As noted in the ME results’ screenshots, our report was accompanied by timely, direct messages delivered to the stakeholders within Cortex XDR (the threat detection and response platform that powers our MDR service), which has continually proven itself a worthy defense solution in all previous rounds of the MITRE Enterprise evaluations.
In the first two pages of the threat report our team answers four of the five critical questions outlined above. The rest of the report provides a deeper look at how the attack was carried out and precisely how the defenders should respond with immediate remediation suggestions and longer-term recommendations to improve their overall security posture to significantly reduce risk of future attacks.
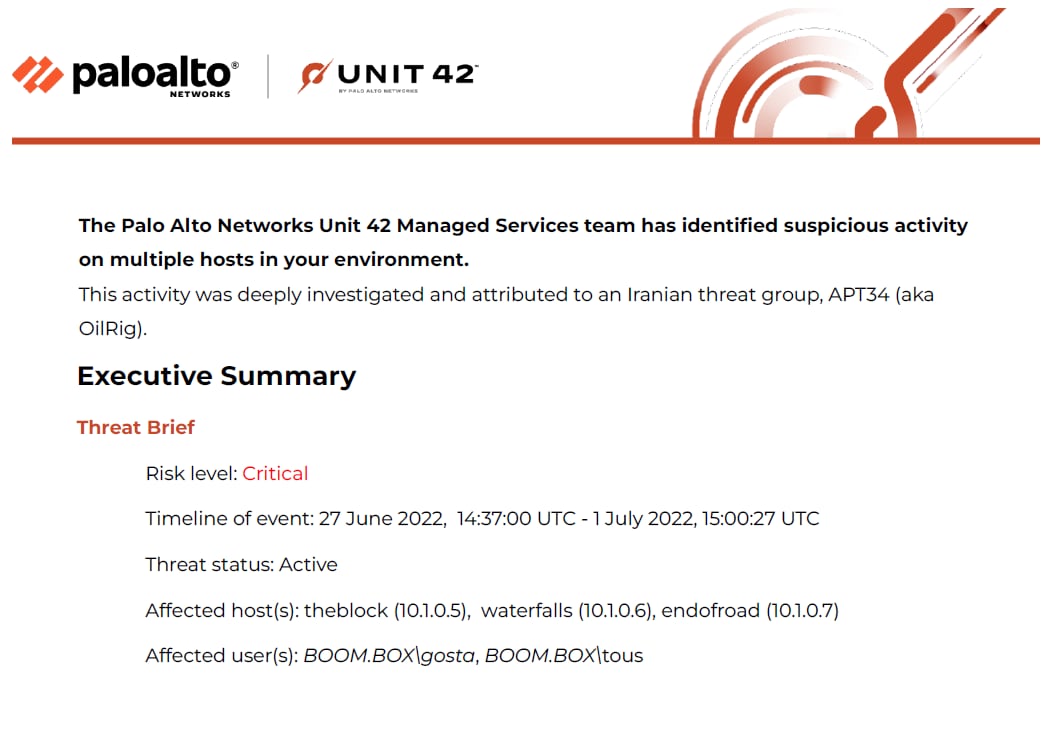
The opening paragraphs of the threat report accurately attribute the adversary as OilRig, identify the impacted users and systems, and also recognize the risk level associated with this attack. The executive summary goes on to describe the complete infection flow and impact of the breach with supporting diagrams to highlight the adversary's movements and TTPs. These include initial access via spear phishing all the way to the exfiltration of the business’ SQL database, which was the adversary’s endgame. Additionally, execution, persistence and discovery techniques are highlighted, as well as the credentials that were compromised and how they were used to further the attack.
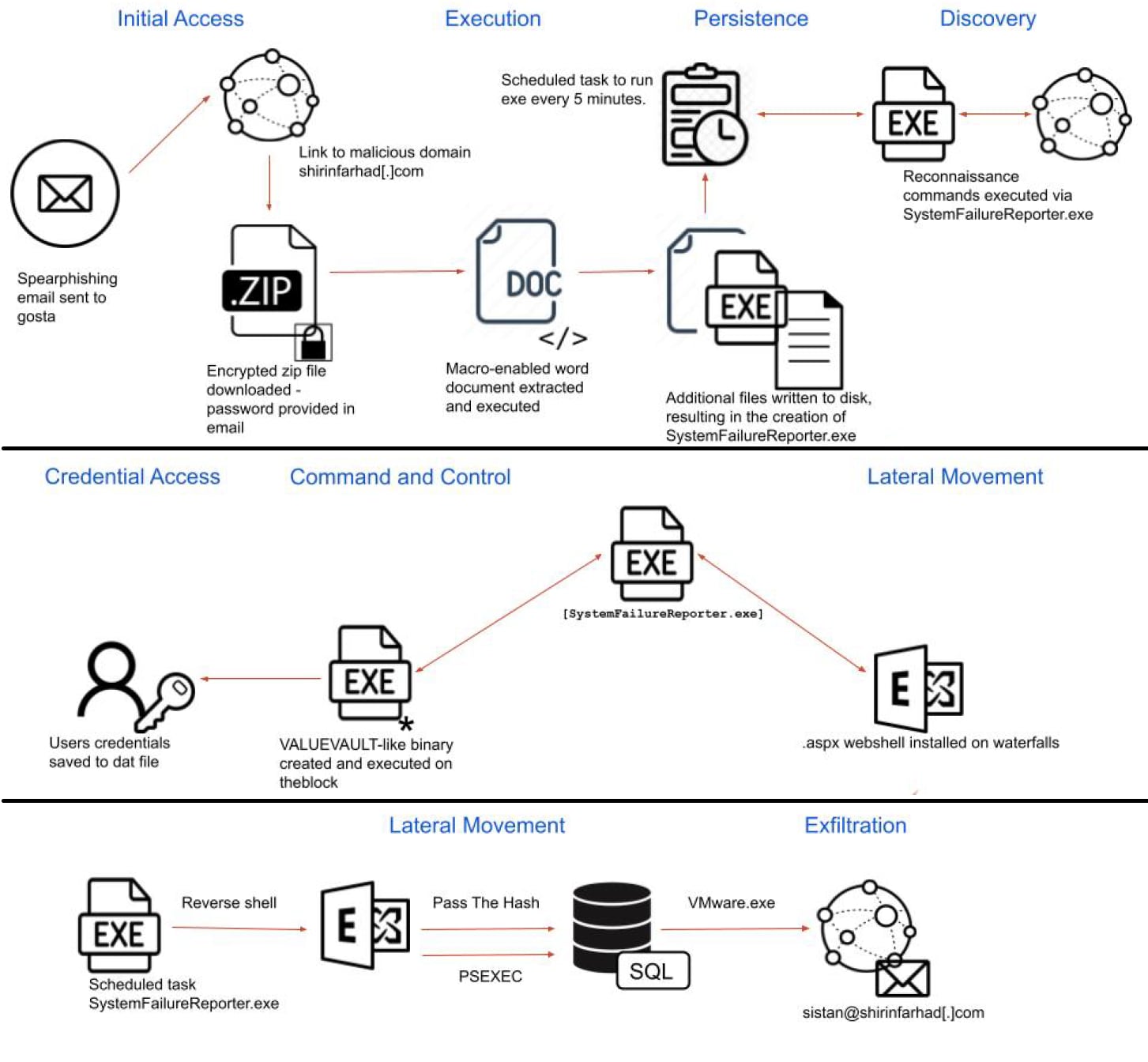
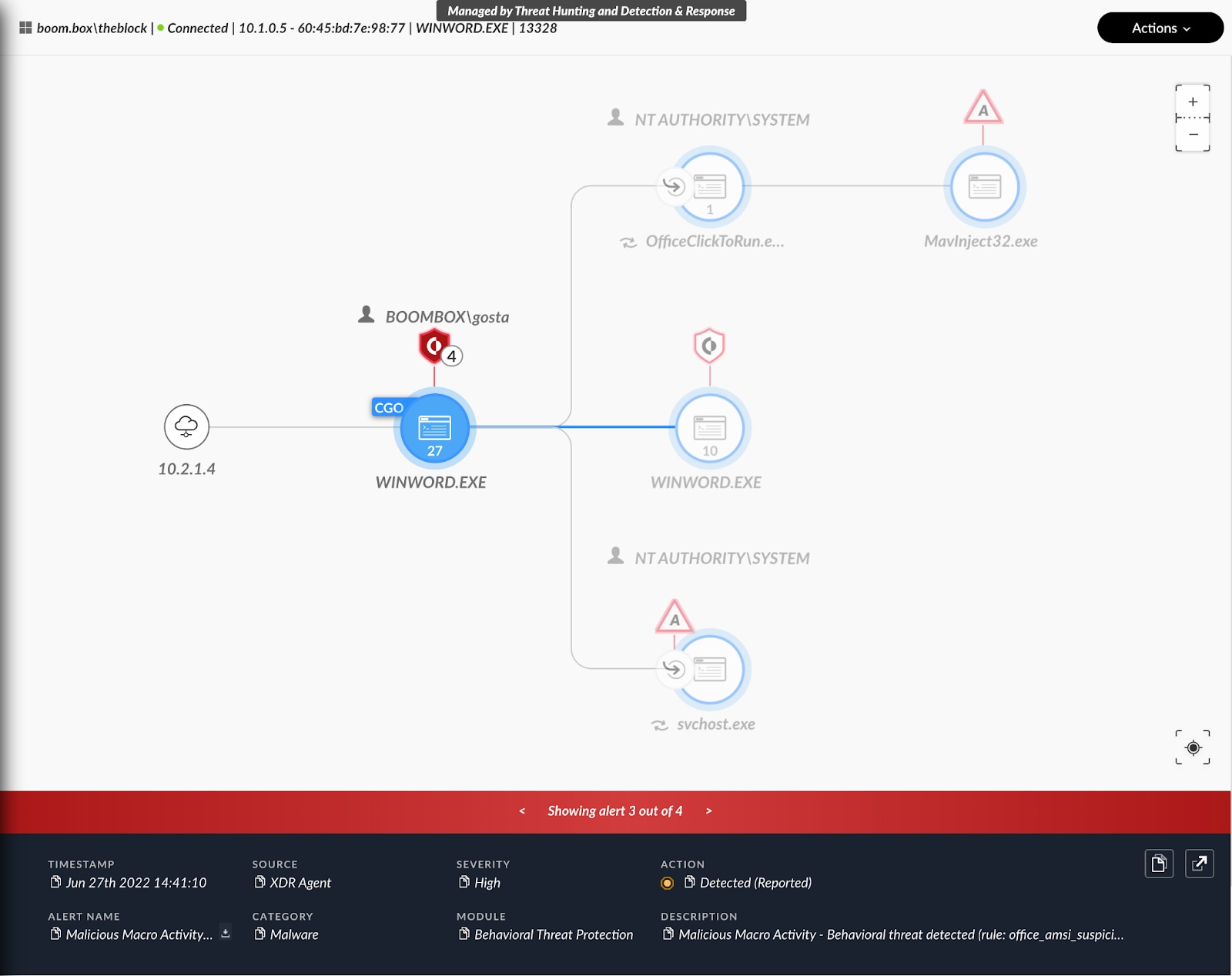
Before the executive summary, the report provides a table of contents, ensuring business stakeholders can quickly find the answers and recommendations they need. After the executive summary, the report goes into detail about each of the TTPs the adversary leveraged. The corresponding impact of each phase of the attack is provided in clear diagrams of causality and process execution, as observed within Cortex XDR (Figure 3 below). A full table of the ATT&CK TTPs used during the attack is provided. Additionally, the report shares the threat hunting queries used by our Threat Hunters, along with guidance on how these can be used for further threat hunting.
The Unit 42 threat report details specifics of the infrastructure used by the adversary throughout the attack lifecycle, noting specifics about private and public domain infrastructure, naming conventions leveraged, as well as origination, destination email addresses and IP addresses. This, coupled with a thorough analysis of all malware leveraged throughout the campaign and the similarities seen in previous attack campaigns culminate in a thorough body of evidence leading to the attribution of OilRig. We also noted obvious deviations observed, given this was a simulation of their attack methodology. Accurate attribution is a critical step as it can guide incident responders in how to hunt for additional TTPs commonly used by the adversary, resulting in a more comprehensive analysis of the attack, which is critical in achieving full remediation.
All of the above leads to probably the most important part of the report – a two-part guide on how a business should respond, providing both the short-term actions to fully remediate the adversary's actions, and the longer-term recommendations to improve their security posture and prevent similar cyber threats in the future.
Unit 42’s experienced team is trusted globally by CISO’s to monitor their environment 24/7 for emerging threats and to ensure their incident response is prompt and effective. Our customers continually provide feedback on how our managed services and corresponding reports have protected them and guided them to confidently respond in the face of real-word attacks. We are excited to share those results with the rest of the community.
Learn more about Unit 42’s suite of managed services, including MDR and MTH, and how we can help secure your organization.