As part of the rapid shift to public cloud, companies everywhere have worked hard to enable engineers to quickly develop and enhance their applications through the use of continuous integration and continuous development (aka CI/CD) infrastructure and processes. It’s incredible how much this has enabled faster development of applications and overall enablement of businesses to move quickly and be responsive to customers. Unfortunately, attackers have recognized this as an opportunity.
The diversity, velocity and dynamic nature of today’s engineering ecosystem have introduced a wide array of new security challenges and gaps, setting the stage for the software supply chain to emerge as one of the most challenging and impactful attack vectors of the past few years. We all know about SolarWinds and Log4j, but there are many more examples that illustrate a significant rise in the number, frequency and magnitude of incidents and attack vectors abusing flaws in the CI/CD ecosystem.
With the big shift toward open source software, much of the attention has rightfully centered on where code comes from and how to secure it. For example, Software Composition Analysis (SCA), which we introduced a couple months ago, addresses the open source portion of the supply chain. But, there's another equally critical component that is often overlooked: securing all of the applications and third-party tools used in the software development pipeline (aka, the CI/CD pipeline).
That is why we have our sights set on reducing the software supply chain attack surface with our proposed acquisition of Cider Security, a pioneer in software supply chain security and an innovator in addressing CI/CD pipeline risk.
The Plight of the Software Supply Chain
The stakes are high when it comes to software supply chain security. A single insecure step or misconfigured tool can expose the entire organization.
Modern cloud-native applications are constructed in CI/CD pipelines consisting of many repos, registries, frameworks, languages, third-party components and dependencies. These pipelines are highly automated, can have hundreds of third-party tools involved, and can have numerous active pipelines before the software artifacts are deployed to the production environment. And, all of these tools have access to source code. Yet, most organizations have limited visibility into the inventory, map and connections of all tools and applications within the software supply chain.
This means that the increasing number of organizations that are reliant upon modern CI/CD development approaches are exposed to several potentially vulnerable tools and applications with access to source code. Yet, for security teams, it is incredibly difficult to gain visibility into what they have, how they are configured, and whether or not they are secured.
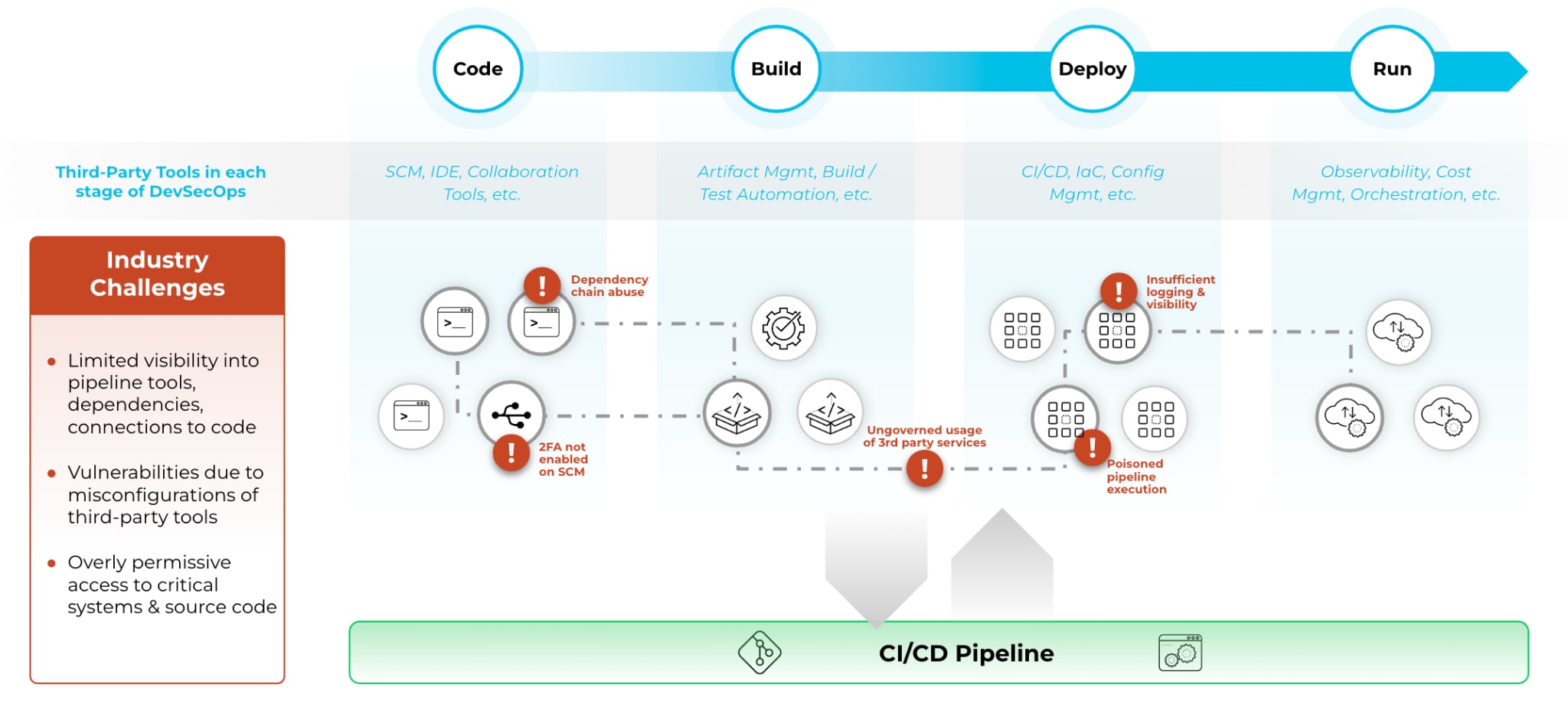
There has to be a better way.
Cider Helps Ensure Cloud Apps Are Developed Securely
Cider has figured out that it’s actually possible to securely connect into the application infrastructure and analyze each of the tools, visualize how they connect to apps and each other, identify where the risks are, and prioritize how to remediate them.
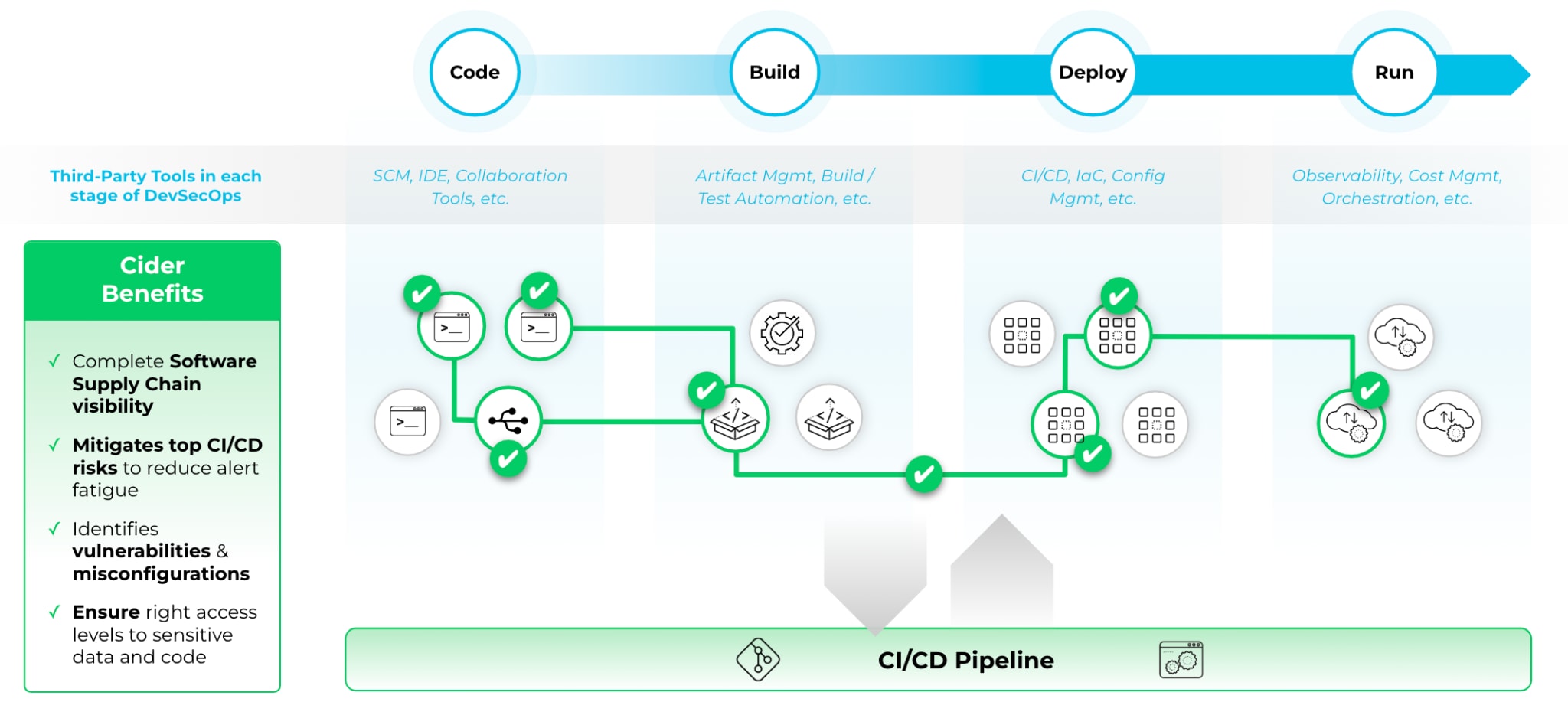
More importantly, application developers and engineers can continue to move fast with security baked into their existing application development process and delivery pipelines, resulting in a seamless and positive user experience for both security teams and developers.
Cloud Security from a Platform or Best in Breed? You Don’t Have to Choose
The proposed Cider acquisition complements the Palo Alto Networks Prisma Cloud platform approach to securing the entire application lifecycle from code to cloud while driving greater collaboration between security teams, DevOps and application developers. Prisma Cloud’s continuous innovation through new security modules, delivered as part of a platform, has enabled our customers to seamlessly grow their security strategy in accordance with their cloud journey. This is accomplished via a unique approach that cannot be achieved by point solutions.
Combined with our recently announced Software Composition Analysis (SCA) capabilities, Cider furthers Prisma Cloud’s mission to be the industry’s most comprehensive supply chain security solution, delivered as part of its code-to-cloud security platform.
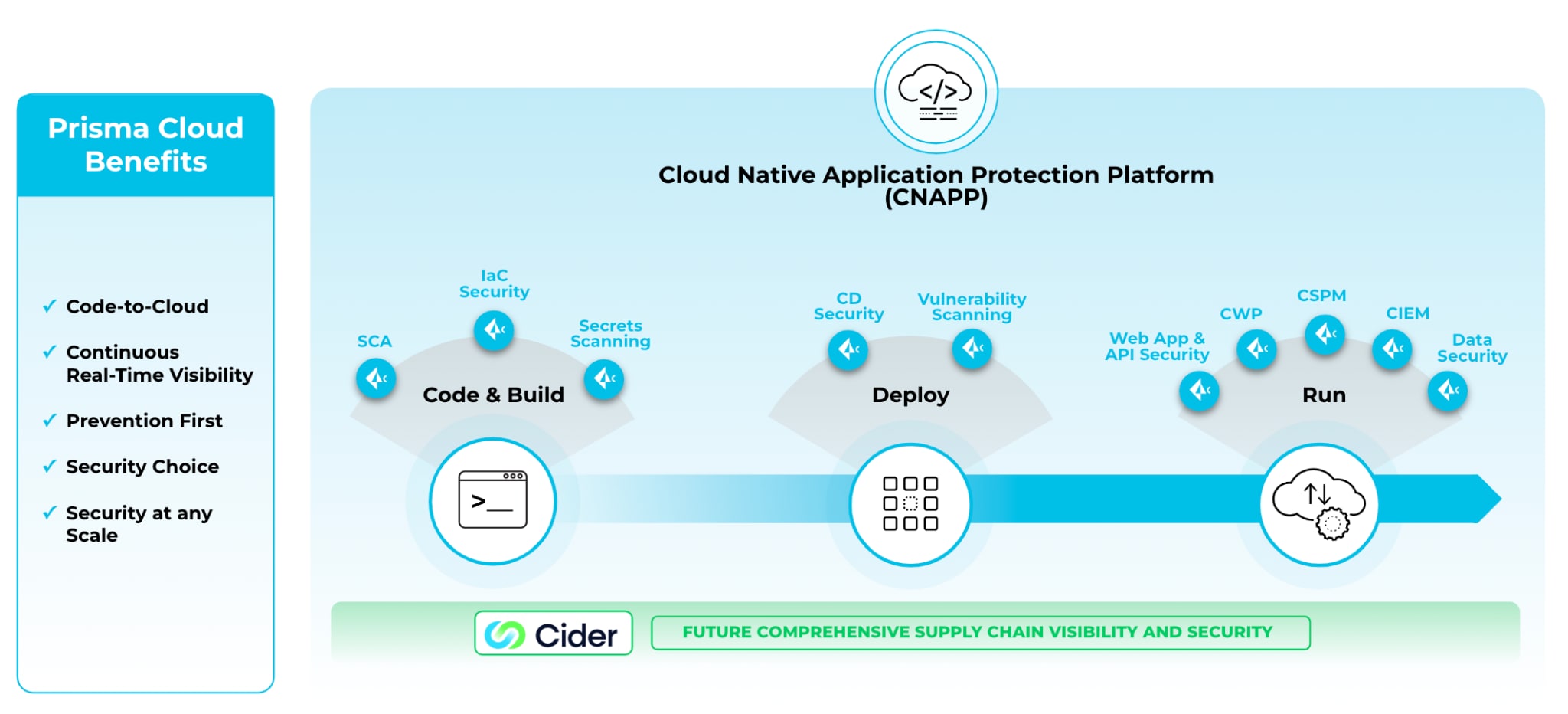
Stay tuned for more information following the close of this acquisition, which remains subject to customary closing conditions.
Forward-Looking Statements
This blog contains forward-looking statements that involve risks, uncertainties and assumptions, including, but not limited to, statements regarding the anticipated benefits and impact of the proposed acquisition to Palo Alto Networks and its customers and future financial and operating results, and the anticipated closing of the acquisition. We identify various risks and uncertainties that could affect forward-looking statements in our Annual Report on Form 10-K filed with the SEC on September 6, 2022, which is available on our website at investors.paloaltonetworks.com and on the SEC's website at www.sec.gov. Additional information will also be set forth in other filings that we make with the SEC from time to time. All forward-looking statements in this blog are based on information available to us as of the date hereof, and we do not assume any obligation to update the forward-looking statements provided to reflect events that occur or circumstances that exist after the date on which they were made.