This post is also available in: 日本語 (Japanese)
The Unit 42 cybersecurity consulting group published research on the first known malware targeting Windows containers, which was discovered by Unit 42 researcher Daniel Prizmant and named Siloscape. It’s extremely stealthy malware that uses sophisticated code obfuscation techniques and communicates to its command and control (C2) server over Tor (open-source software for enabling anonymous communication) to hide its presence. Unit 42 researchers have previously only seen malware targeting containers in Linux due to the popularity of that operating system in cloud environments. Unit 42 has identified 23 Siloscape victims and discovered evidence that the campaign has been taking place for more than a year.
Containers provide an easy way to run applications in the cloud. Just as cargo ships have containers that package many different materials together for efficiency, containers in the cloud carry a similar function in that they allow development teams to move faster and operate at almost any scale. The process of running an application in a container is called “containerization.” We’ve seen more and more organizations using containers in the cloud in recent years, especially since the COVID-19 pandemic caused many to seek to move faster and deploy cloud workloads more efficiently.
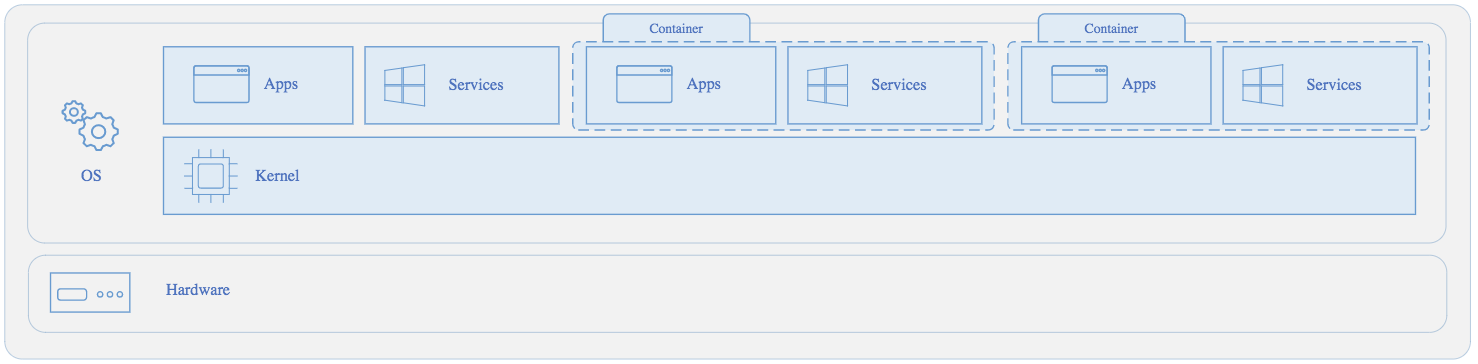
In addition to containers, there are clusters. A cluster is the basic architecture of Kubernetes (an open-source container platform). A Kubernetes cluster is a set of machines, known as nodes, that run containerized applications.
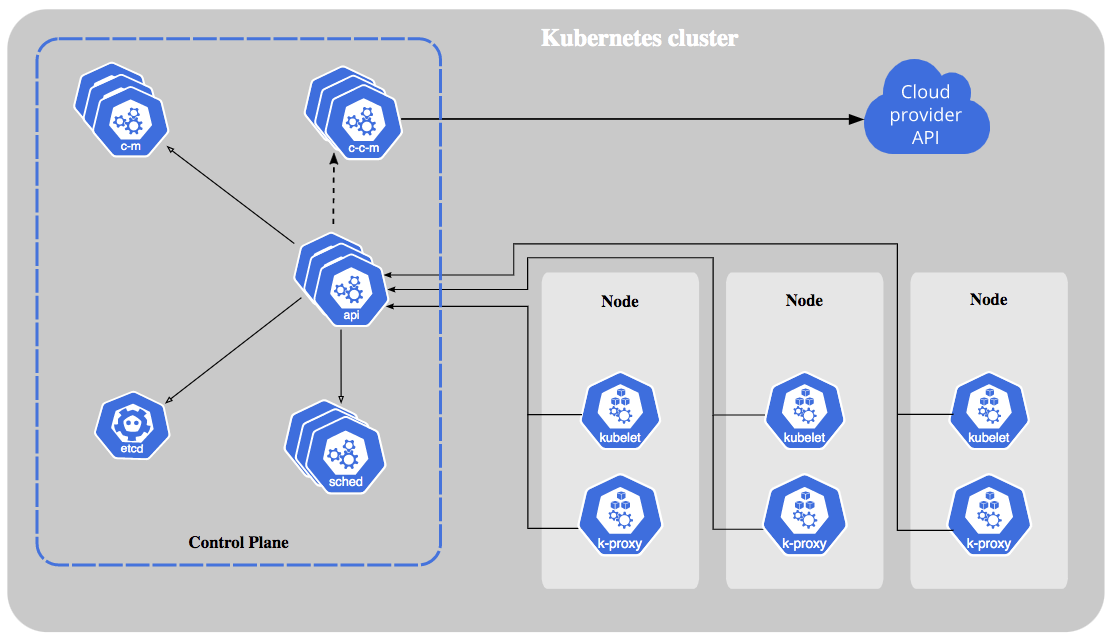
Siloscape targets Windows containers and opens up a backdoor to a Kubernetes cluster. This then gives an attacker access to run any code, anywhere in the victim’s cluster. An attacker could conduct a wide variety of attacks against an organization, for example, ransomware (by locking/encrypting the cluster), cryptojacking (by using cloud computing power), distributed Denial of Service (DDoS) (by using cloud computing power as part of a botnet) and data exfiltration (by stealing data within the cluster). Even if a single container within the cluster gets shut down, the attacker is still in control. They can create new containers, execute code in existing containers or shut down others.
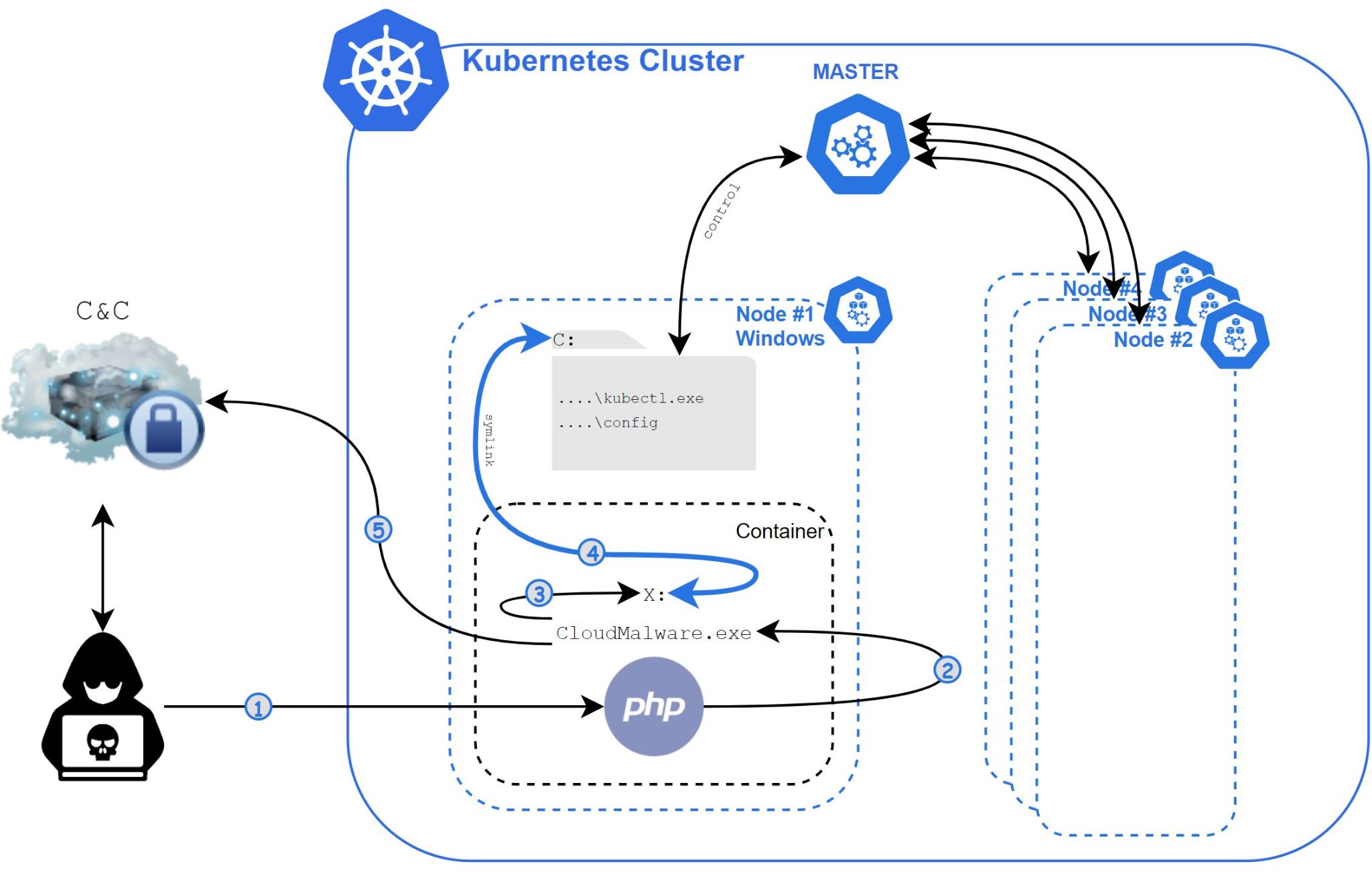
Siloscape could wreak havoc in a Windows cloud environment by compromising a Kubernetes cluster.
For organizations running Windows containers, we recommend the following:
- Follow Microsoft’s guidance recommending users not run anything in a Windows container that they wouldn’t be willing to run as an admin on the host.
- Limit the privilege of each node by using the Kubernetes Authorization modules, such as role-based access control (RBAC).
- Make sure all of your deployments are using the latest version of all of their applications and frequently scan for security releases with a Cloud Native Security Platform (CNSP) such as Prisma Cloud.
For more information, read the Unit 42 report, “Siloscape: First Known Malware Targeting Windows Containers to Compromise Cloud Environments,” or register for the June 9 webinar, when Unit 42 researchers will take a live deep dive into how to protect against Siloscape. To learn more about Prisma Cloud, please visit our new website.
