How Palo Alto Network’s Next-Generation Firewalls Protect Against Torpig Attack
In this blog, I talk about how our next-generation firewalls protect against botnets such as Torpig. There are 3 parts to a botnet attack:
1. User visits a website which starts a chain reaction for torpig-infection
There are 2 ways in which this can happen:
a. User is tricked into going to a website that he/she didn’t intend to go in first place
This is also known as a phishing attack. Once the user visits such a website, the website would start downloading exploits to user’s computer without user’s intervention. Such downloads are also referred to as drive-by-downloads in the sense that the user didn’t have to explicitly download the exploits; just by the virtue of visiting the website would cause the download to happen.
Such attacks can be usually nipped in the bud by a URL filtering solution that would detect user’s traffic going to a pre-categorized malware website. Our next-generation firewalls provide URL filtering solution that can help in detecting such traffic and thereby preventing the attack.
b. User goes to a popular website that has been recently hacked into
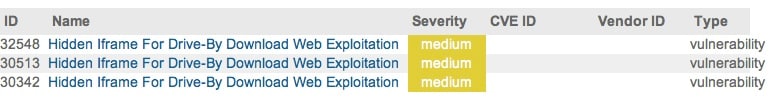
This happened recently with songlyrics.com. The website was hacked into and the HTML content of the website was modified to include a malicious <iframe> that in turn directed the user’s browser to go to a malware hosting site. Note that <iframe> by itself is not harmful, in fact it is part of standard HTML specification. It's just that some usages of <iframe> could be malicious and as such it is important that any signatures protecting against malicious <iframe> are written such that they don't generate false positives. Palo Alto Network's next-generation firewalls currently have three such signatures to detect malicious iframes.
<above information is available on support.paloaltonetworks.com website under "Threat Database" link>
2. The <iframe> in the page directs the user machine to go to a malware site and download exploits
As mentioned earlier, the <iframe> would direct user’s browser to a malware hosting site, which can once again can “very likely” be caught by the URL filtering solution. I mentioned “very likely” because it depends on how long the malware website has been up; if the website is very recent, it is possible that the URL filtering database has not yet tagged the website as malicious.
In any case, lets assume for now that the URL filtering does not stop the traffic. Now the malware site will start throwing exploits at the user’s computer trying to exploit an un-patched or even zero-day vulnerability. Once that vulnerability is found, the malware site would download the actual malware/virus to the computer that will cause the computer to become a “bot”.
Our next-generation firewalls can stop such an attack using our vulnerability-based signatures. Here, it is important to distinguish between vulnerability-based signatures versus exploit-based signatures. A single vulnerability-based signature can protect against all different attacks that try to take advantage of that vulnerability. Exploit-based signatures, however, protect against only certain attack vectors. Clearly, it is desirable to have vulnerability-based signatures as they provide the most comprehensive protection.
At Palo Alto Networks, our threat team spends considerable time in understanding vulnerabilities and creating signatures to protect against the vulnerability itself. In fact, Palo Alto Networks Threat Team has been recognized several times by Microsoft for discovering and reporting Microsoft related vulnerabilities. Palo Alto Networks is the only private company in the top 5 list of companies that have reported vulnerabilities to Microsoft.
Additionally, customers should be mindful of the packet latency when vulnerability protection is turned on. Due to its single-pass architecture, Palo Alto Network's next-generation firewall scans the contents only once, the results of which are used in vulnerability/spyware/virus blocking, file blocking and URL filtering. Particularly our antivirus solution is stream-based versus being file-based. File-based antivirus solutions first download the entire file and then run virus checks on the file. This results in increasing packet latency through the device. Stream-based solution does virus checking while the file is in transit. Clearly, the latter solution would be preferred from user perspective.
Coming back to exploits, once the user’s machine is successfully compromised, the malware website then downloads an executable file (virus) which in case of Torpig causes installation of Mebroot. Most IPSes do not cover virus protection. Palo Alto Network's next-generation firewall, however, provides strong antivirus solution. We receive several thousand virus samples from our partners. Our threat team analyzes the samples, looks for malicious patterns in the files and then subsequently defines virus signatures that detect several samples. This helps in reducing virus signature footprint.
Specifically for Torpig, we have over 6400 signatures to capture torpig-related malicious executable files. These signatures provide coverage against roughly 12,800 malicious samples (each torpig signature on average covers 2 samples).
3. The malicious code installed on victim computer sends personal info to Torpig’s Command and Control servers
This is the step that makes money for the hacker (by stealing personal financial information from the victims).
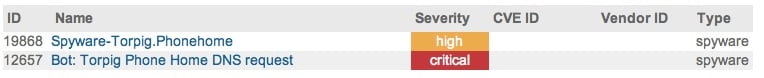
Currently, we provide three signatures to capture such traffic. Once again this is a cat-and-mouse game between hackers coming up with different traffic profiles for connecting to command and control servers and anti-spyware vendors blocking such traffic with unique signatures.
In the picture above, 2nd signature (12657) corresponds to the DNS traffic that our threat team identified to be corresponding to Torpig DNS requests.
Following is the packet dump for DNS traffic from Torpig: The blue part is IP header; red part is UDP header and the rest is DNS response. As you can see from the packet, one of the name servers (which is actually the authoritative server) is torpig.sinkhole.org.
0000 00 16 d3 2d 22 b4 00 18 73 d7 08 5d 08 00 45 88 ...-"... s..]..E.
0010 00 71 00 00 40 00 33 11 0b 93 c0 36 70 1e 0a 01 .q..@.3. ...6p...
0020 01 0c 00 35 46 e4 00 5d 24 13 00 08 80 00 00 01 ...5F..] $.......
0030 00 00 00 02 00 00 08 79 61 7a 74 69 72 70 61 03 .......y aztirpa.
0040 6e 65 74 00 00 01 00 01 c0 0c 00 02 00 01 00 02 net..... ........
0050 a3 00 00 19 03 6e 73 31 0f 74 6f 72 70 69 67 2d .....ns1 .torpig-
0060 73 69 6e 6b 68 6f 6c 65 03 6f 72 67 00 c0 0c 00 sinkhole .org....
0070 02 00 01 00 02 a3 00 00 06 03 6e 73 32 c0 2e ........ ..ns2..
We created a signature to catch such DNS responses. Now, whenever the signature is triggered in a network, one can be pretty sure that they have torpig-infected systems in their network.
Overall, to effectively block or mitigate such attacks, any threat prevention solution needs to be comprehensive without significant performance degradation. Our next-generation firewalls combine all elements of threat prevention together (URL filtering, Vulnerability-attack protection, Spyware protection, Virus protection) at hardware-accelerated speeds and provide risk mitigation for botnet-related attacks.
External links for Torpig:
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.